Praise to Allah who is honoring Islam with his victory, dishonoring polytheism with his defeat, resolving issues by his order, dragging the infidels with his cunningness He who made what goes around comes around with his justice, who gave Wellness to the pious with his grace Prayers and peace upon who Allah raises the light of Islam by his sword and his companions and their followers by beneficence till the Day of Judgment
How to use VeraCrypt program to encrypt Files and Disks
📑 Article Index |
3- How to create an encrypted container.
4- Hide the container and program - to mislead the enemies.
5- Set up a hidden container (extra) inside the main container.
6- How to encrypt System disks and External Memory.

Encrypting files is necessary to protect your data and files from hackers, or physical access. So if the attacker hack your computer, He can not decrypt your personal data encrypted with VeraCrypt because the program relies on strong encryption algorithms.
VeraCrypt is an open Source program and a modified version of the TrueCrypt encryption program where TrueCrypt developers stopped developing the program after government agencies put pressure on them. Veracrypt has undergone security checks and source code checks by many security researchers and companies specializing in information security such as Quarks Lab. Although security vulnerabilities have been discovered in VeraCrypt recently, developers have been working on issuing stable versions to close detected vulnerabilities, making it an important step in the right direction in the filed of electronic protection.
--------------------------------------------
firstly: Download VeraCrypt
------------------------------------------
❍ To download it from official website click here
❍ Then press DOWNLOAD to begin
❍ After the download is completed, you will find the installation file in the Downloads folder
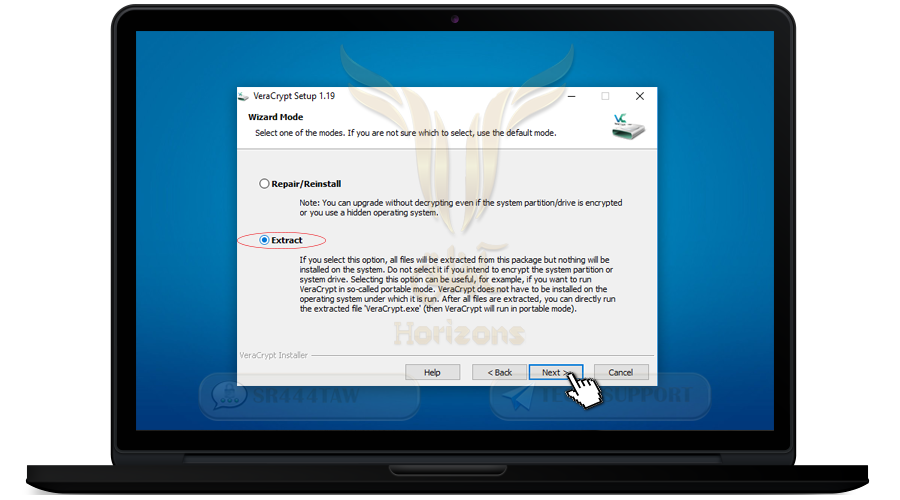
❍ Open the file and select Extract to extract the files and press next
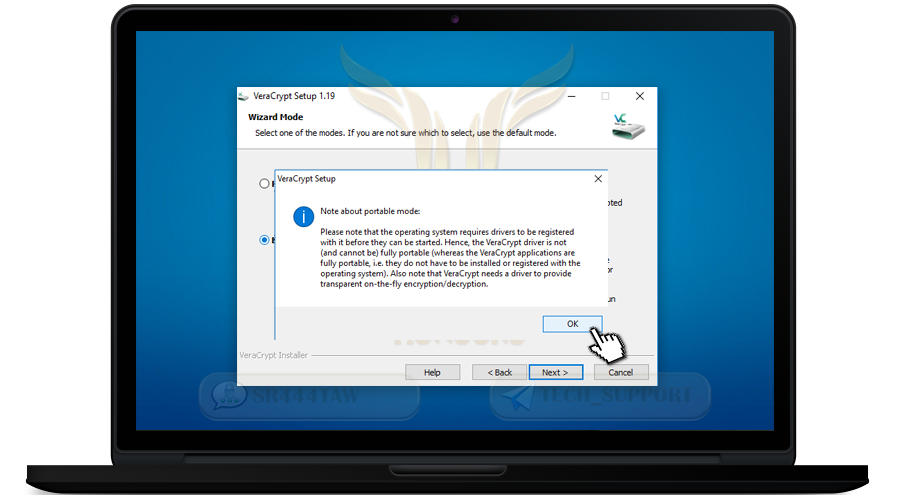
❍ Press OK
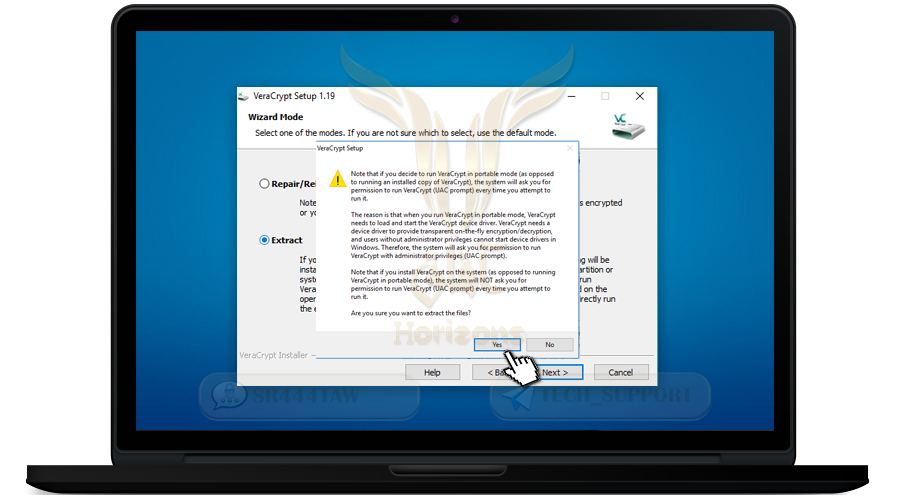
❍ Press Yes
❍ The program will extract the files in the default Downloads folder
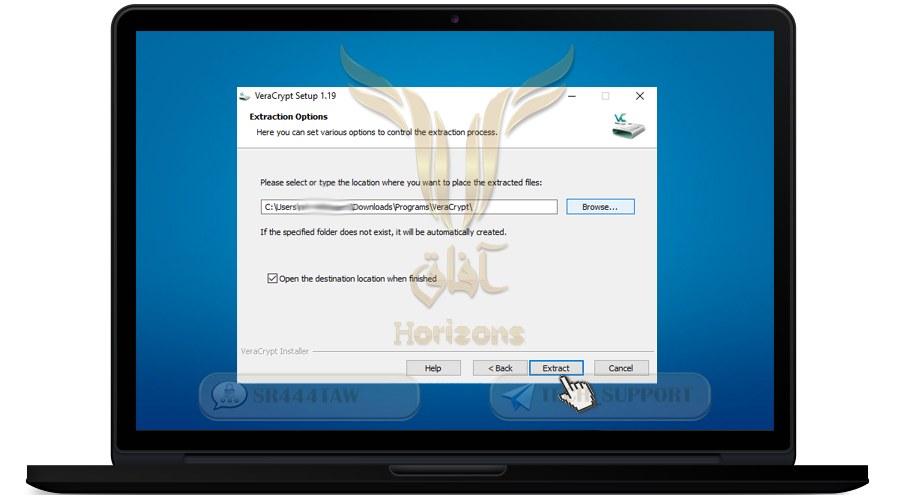
❍ You can also choose folder where you want to extract files by clicking Browse
❍ Press Extract
--------------------------------------------
secondly: Install VeraCrypt
----------------------------------------------
❍ Firstly, delete the program that you downloaded from the site, because we have extracted the required files and If your computer is hacked, investigators do not know about VeraCrypt, and then continue to install VeraCrypt through extracted files
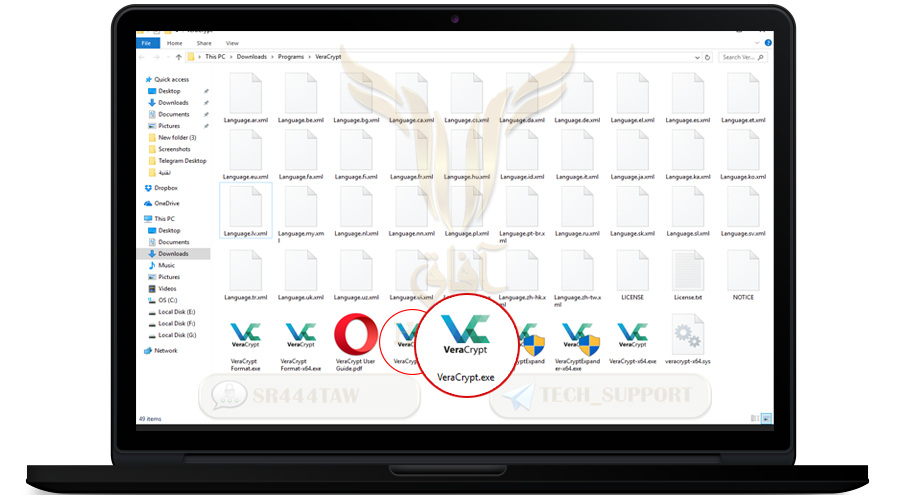
❍ Go to the path where you extracted the files and you will find a folder named VeraCrypt
❍ You will find many files inside
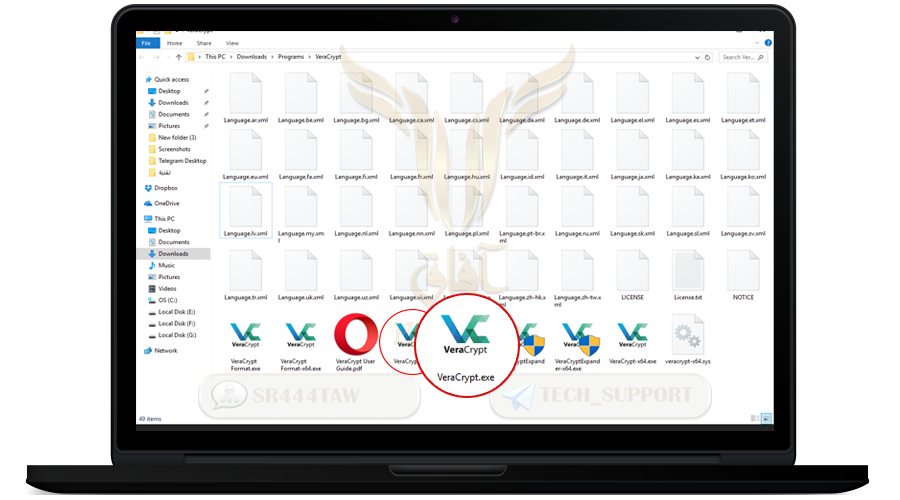
❍ Click VeraCrypt-64x.exe If your processor core 64-bit, if the processor core is 32-bit , press VeraCrypt.exe
💡 Note:
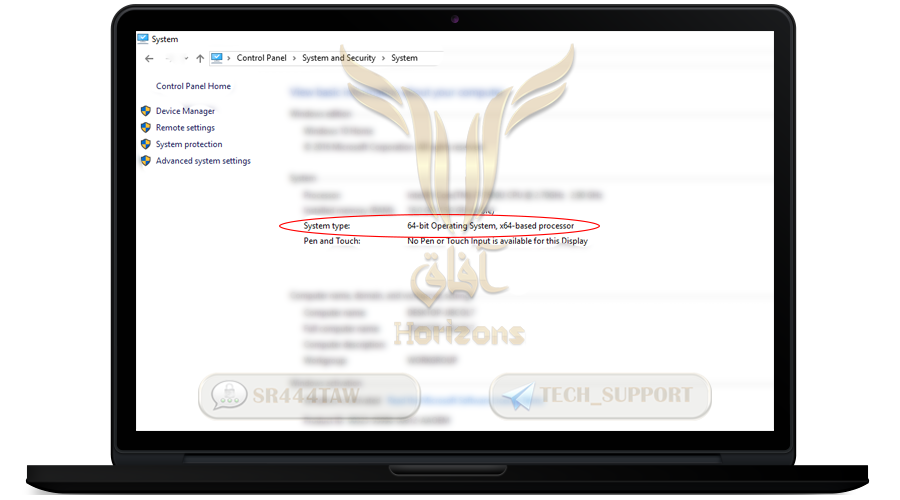
To see the type of processor kernel for your device go to:
ControlPanel> System and Security> Security
----------------------------------------------------------------
Thirdly: How to create encrypted Container
----------------------------------------------------------------------
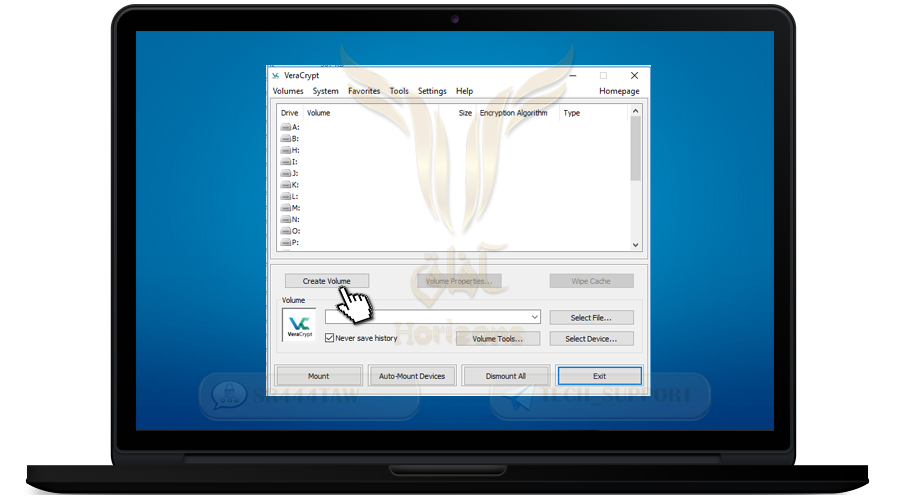
❍ Select Create Volume to create the encrypted container folder
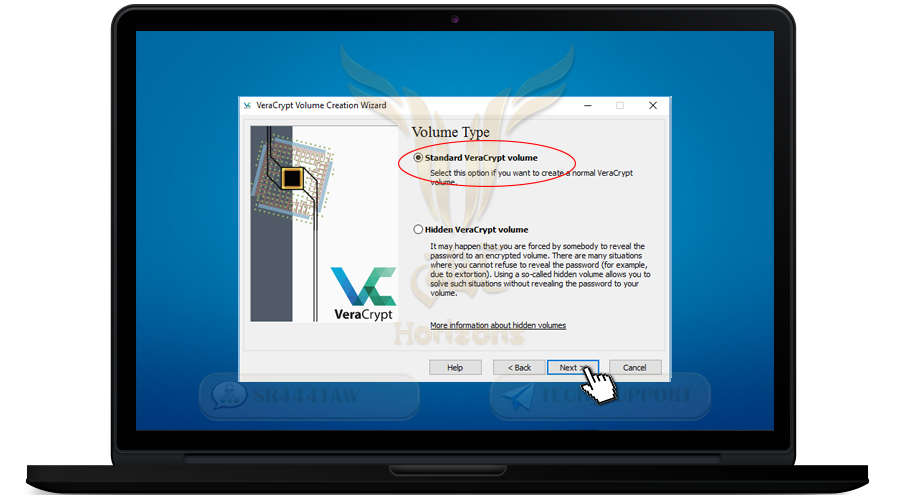
❍ Select Standard VeraCrypt volume and click Next
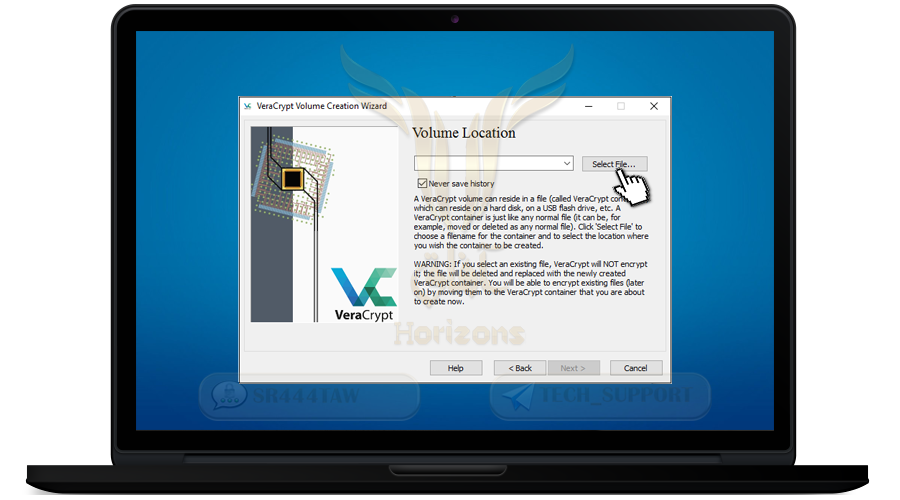
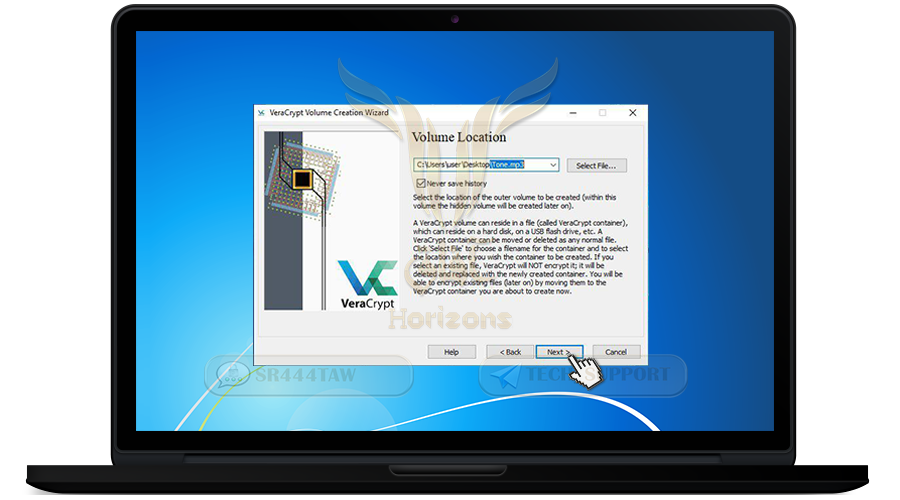
❍ Press Select File and select where you want to create the encrypted container inside to place the files
💡 Note:
A container folder is an encrypted folder that encrypts all the files you move inside
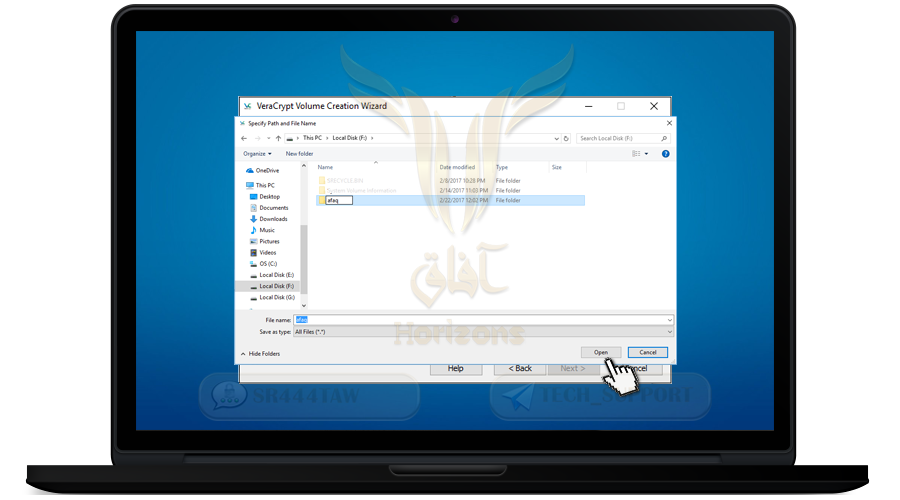
❍ After selecting the folder, press Open
❍ Then click Next
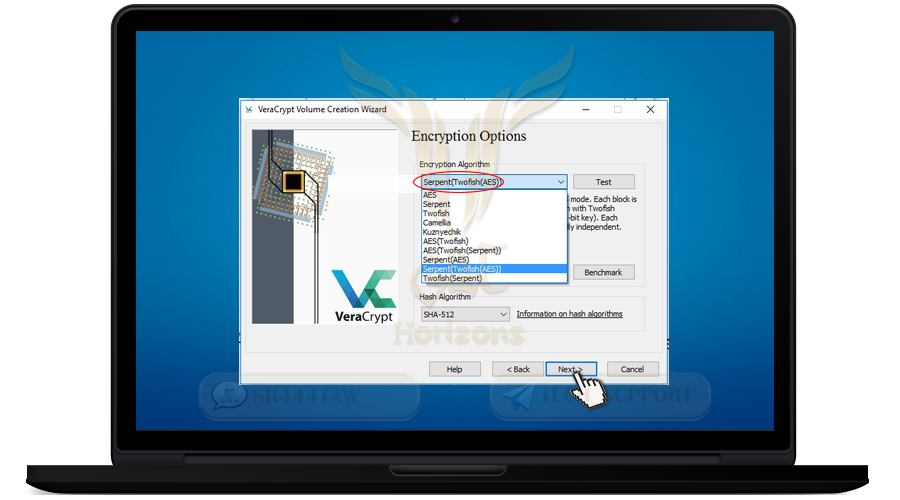
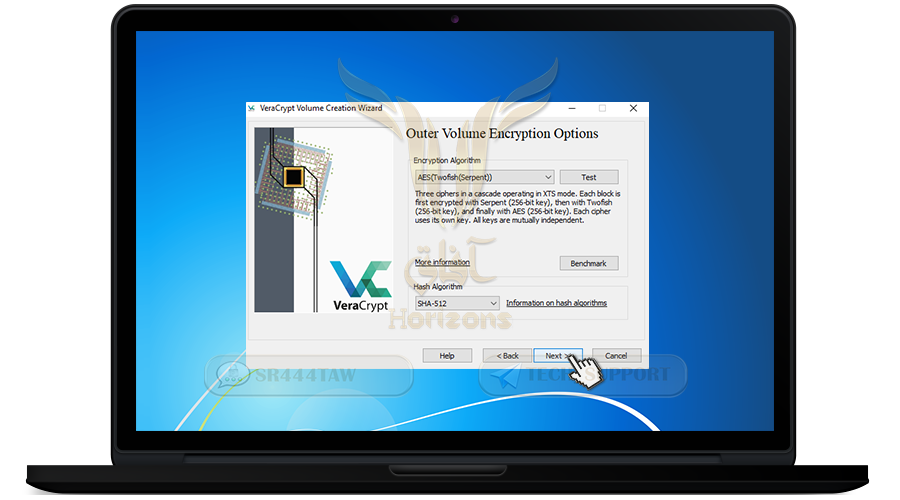
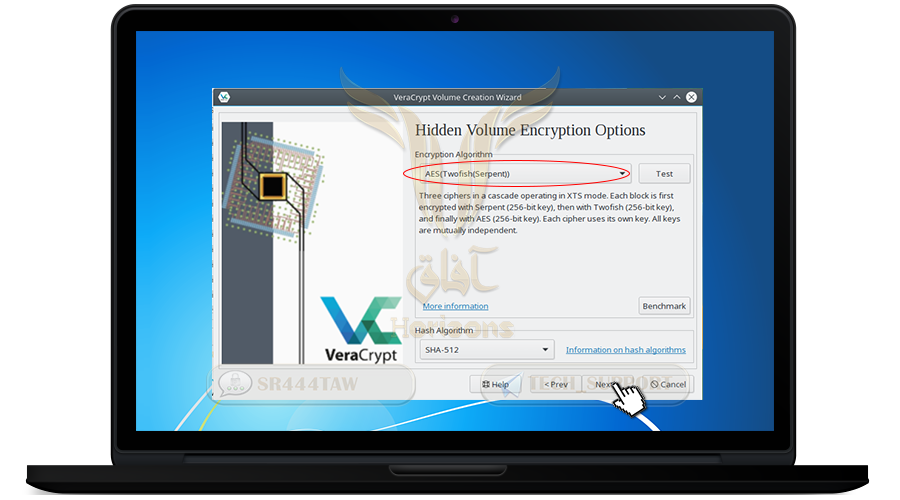
❍ Now we will choose encryption algorithm
❍ Select AES-Twofish-Serpent, this option to encrypt files with 3 algorithms, if the attacker can decrypt one algorithm will not be able to decrypt the other algorithms
❍ Then click Next
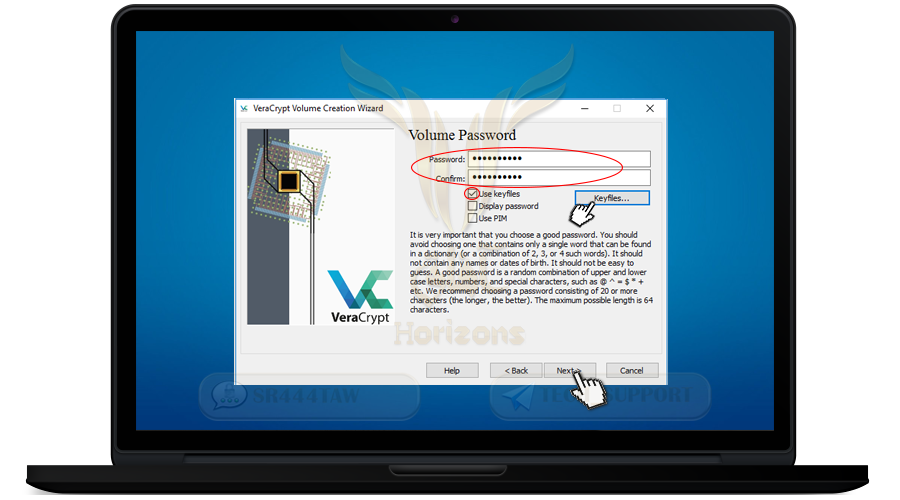
❍ Enter a strong password and confirm it in the second box and press Next
💡 Note:
You can also add a file or image or code if you have lost the container password (optional) where the file serves as a key to open the folder of the encrypted container
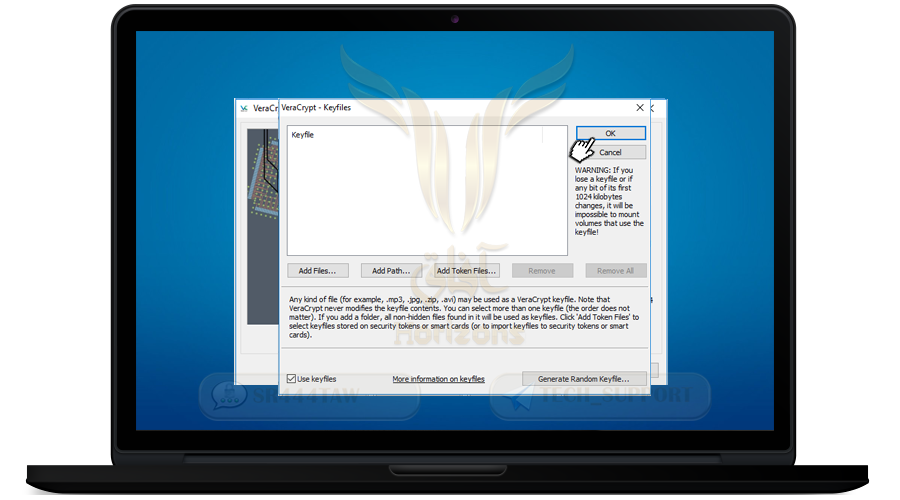
❍ To add a file or image mark Use key files option and press Key file
❍ Select the file or image or PGP key and press OK
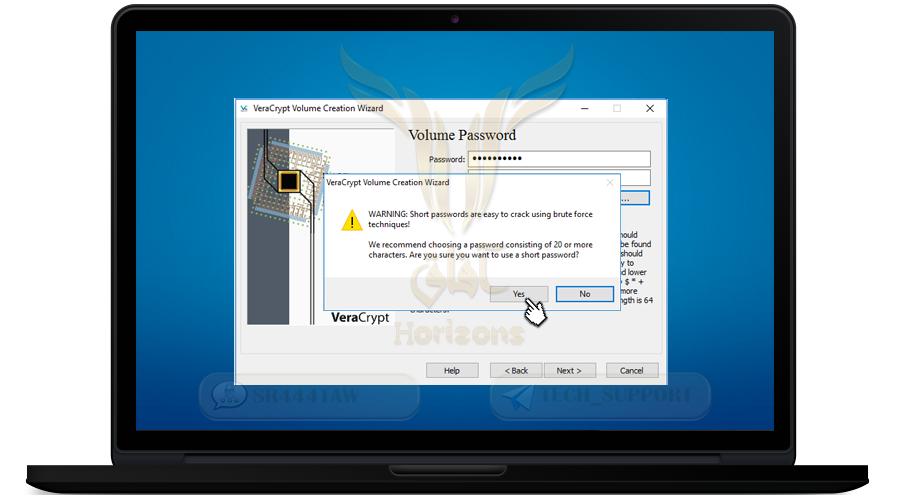
❍ After typing the password (if less than 20 characters) the following message will appear: Click Yes
❍ Select Yes and press NEXT
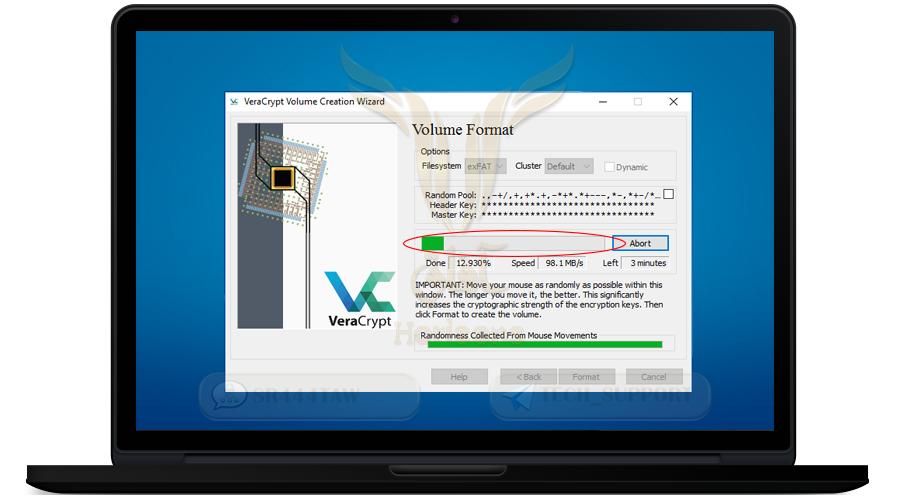
❍ Now the program will encrypt the container file. move the mouse randomly
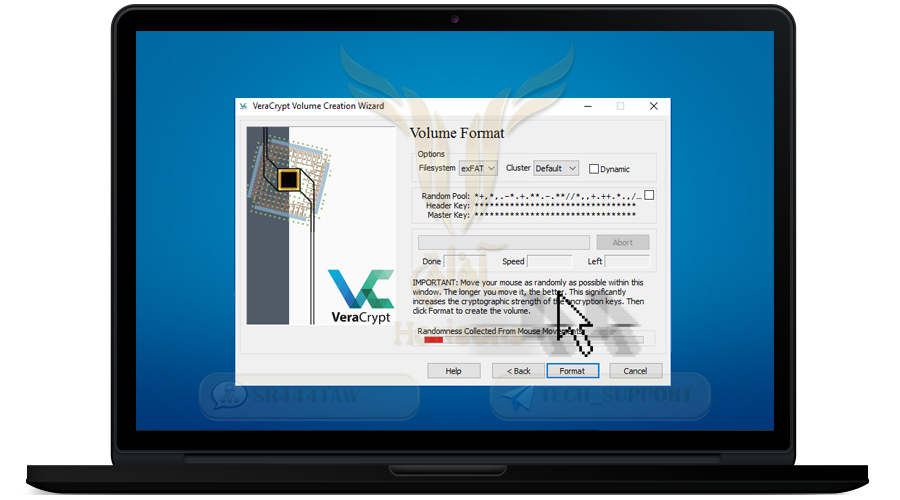
❍ Continue with random movement until the green line is complete
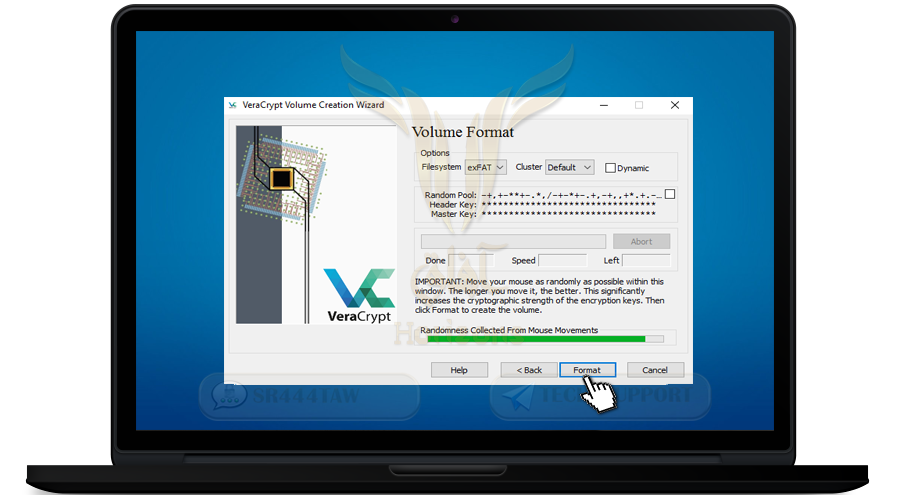
❍ Then press Format to create the container
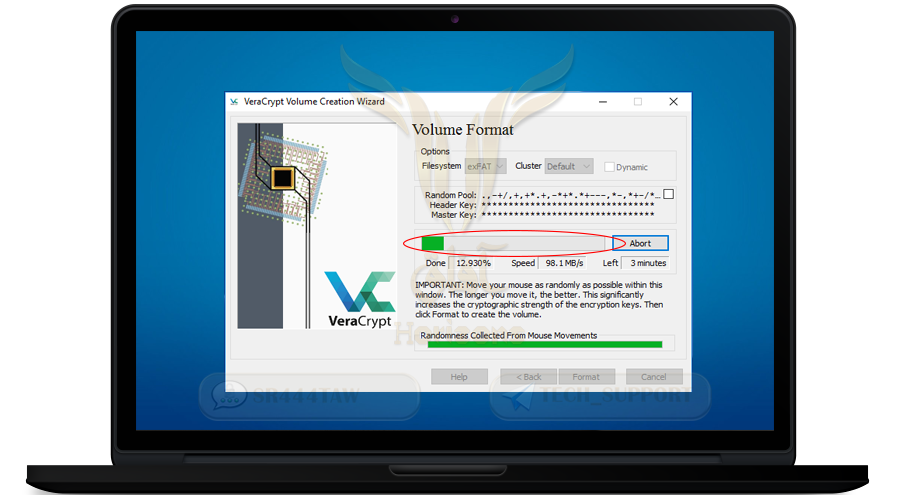
❍ Thus the encrypted container was created
❍ Click Next
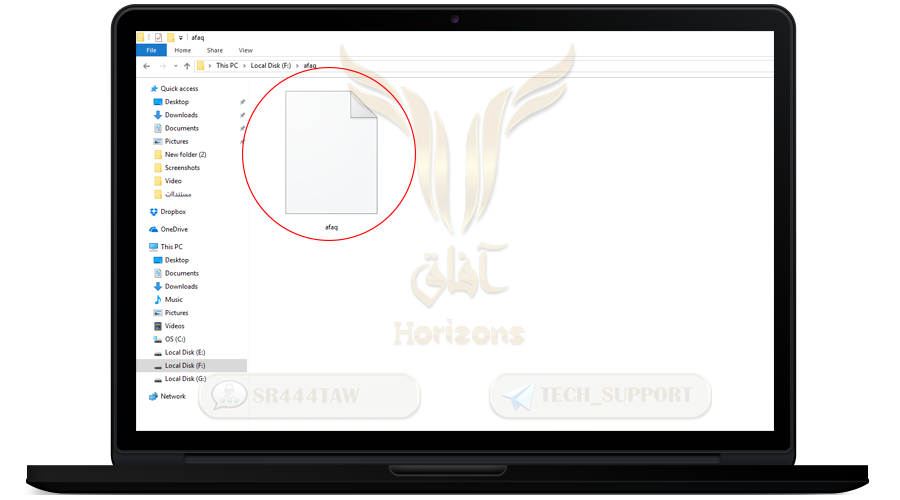
❍ The program ended the creation of the encrypted folder named afaq for use in encrypting the important files inside it as shown in the following picture
❍ Now go back to the interface of the program by going to the VeraCrypt folder
❍ Firstly delete all the attachments in the folder and leave only the main program file (depending on the kernel of your device)
❍ Open the program
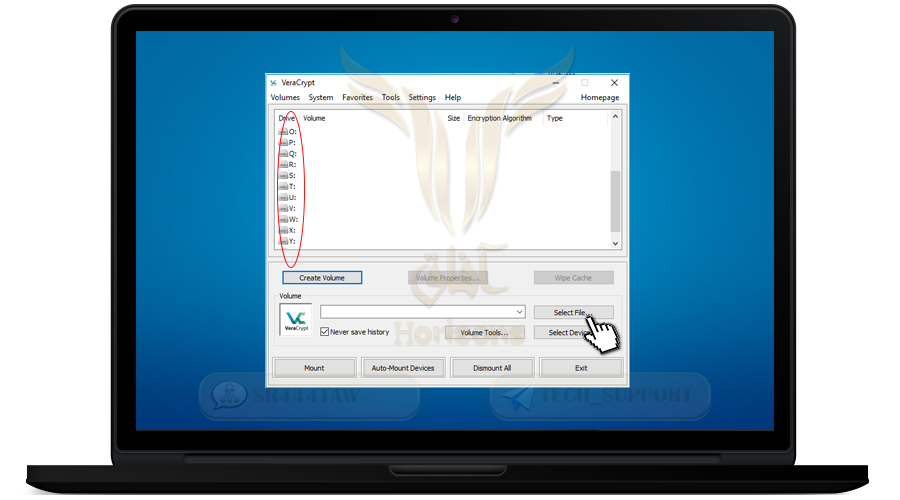
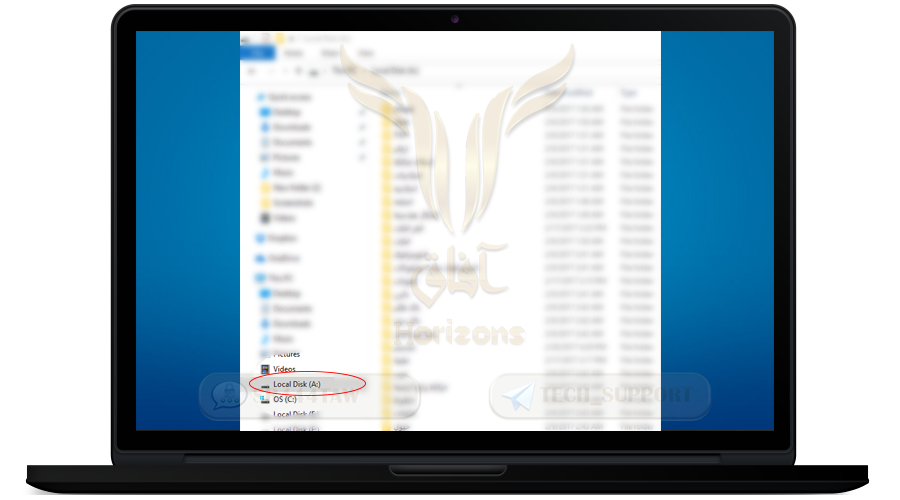
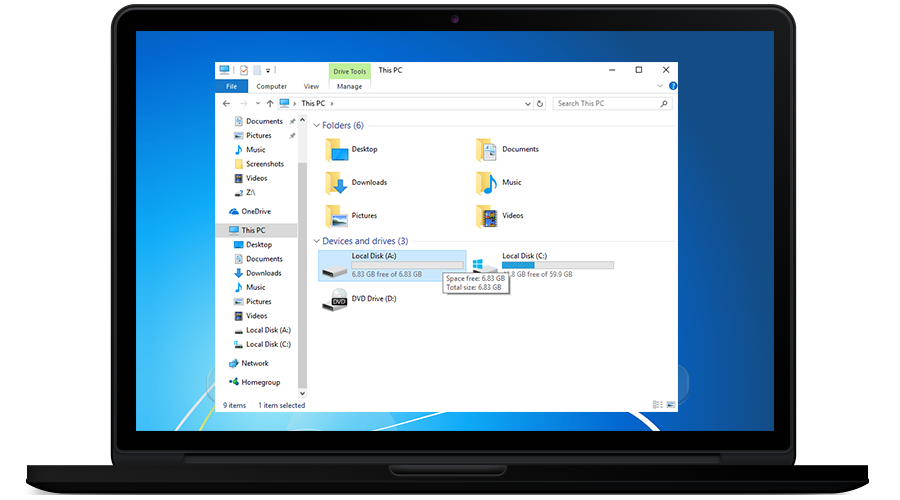
❍ First select one of the disks (the container will appear after we open it with the same disk name as you specified)
❍ Select, for example, disk A:
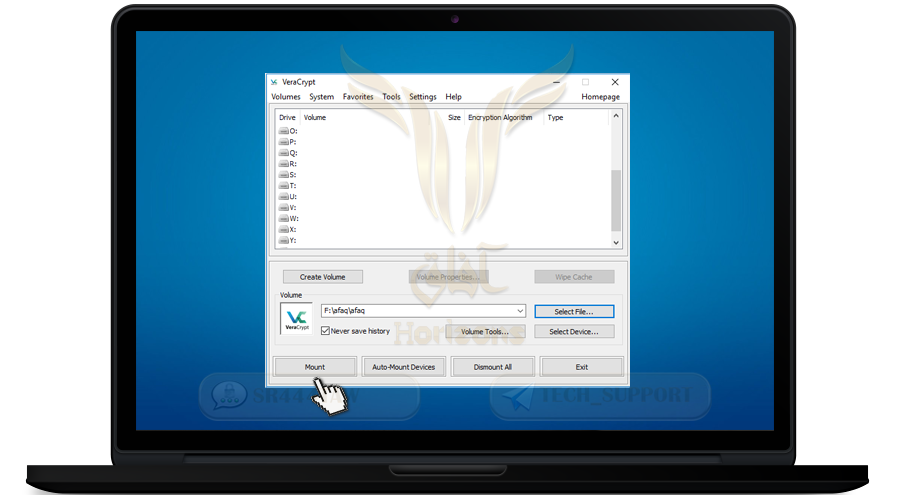
❍ Then click Select File and select the encrypted container file that we just created
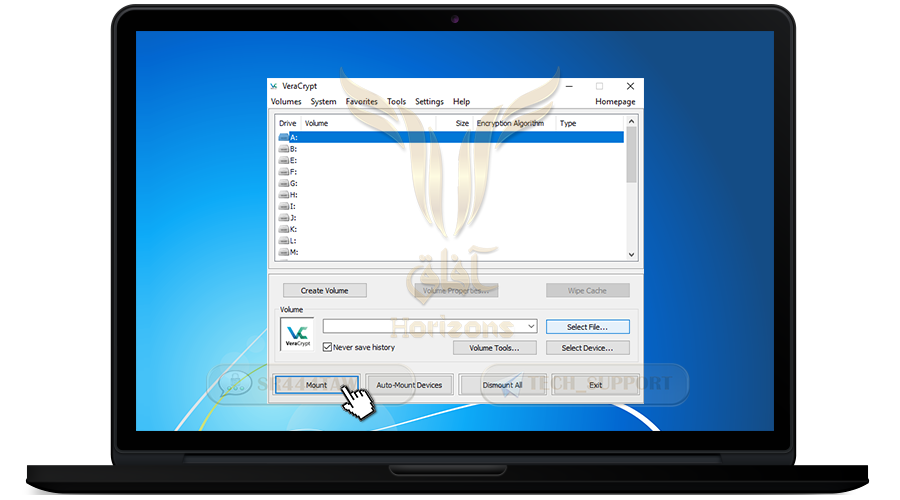
❍ Then press Mount
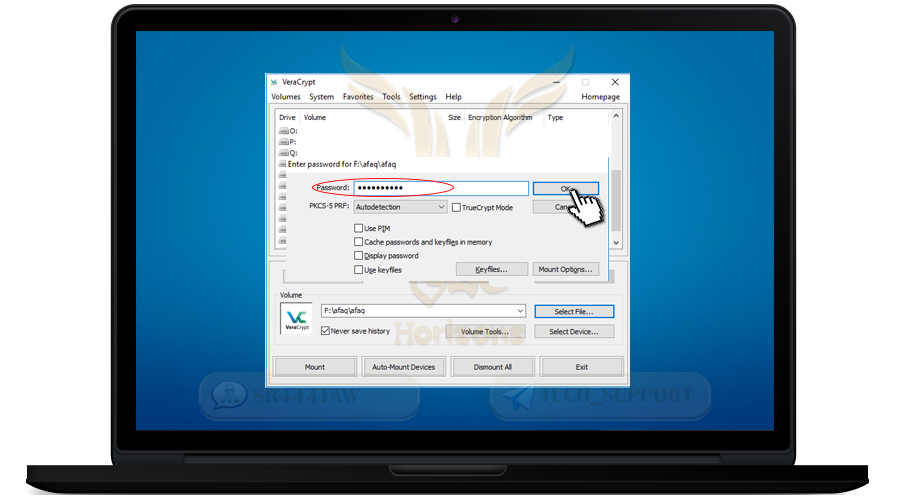
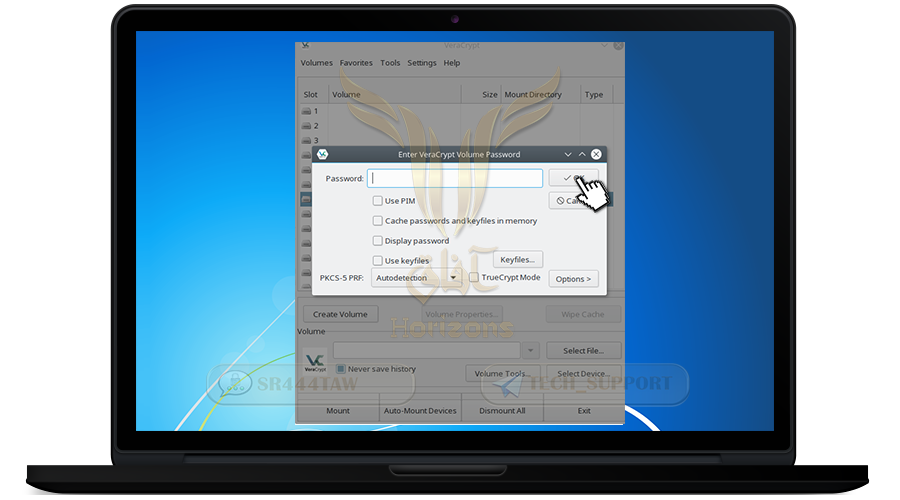
❍ Enter the password you registered when creating the container
❍ then press Ok
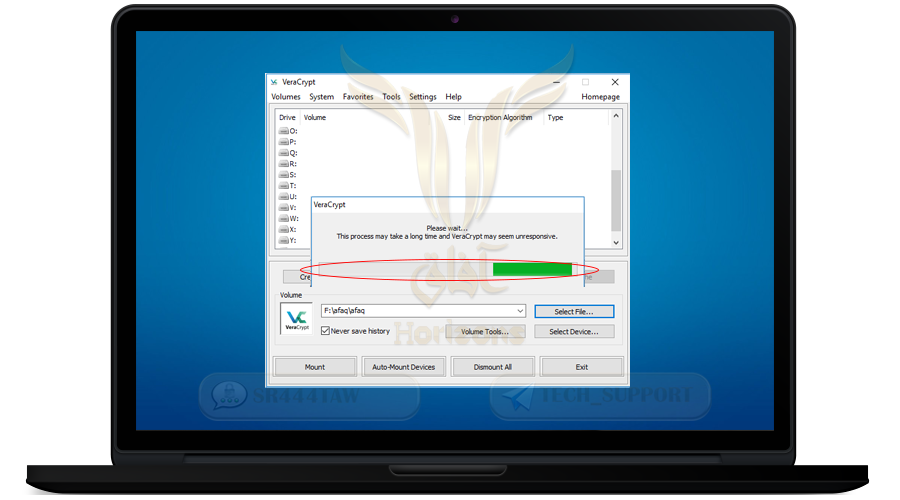
❍ Wait until the encrypted folder opens
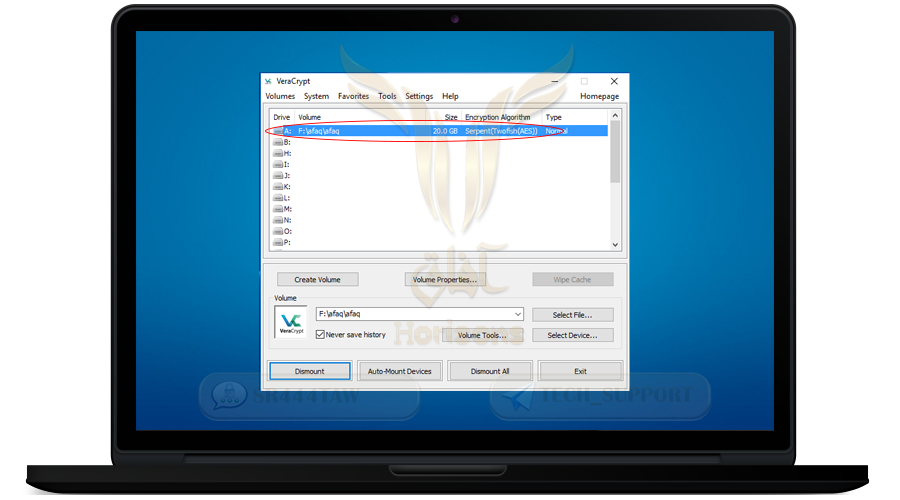
❍ Thus, the folder of the encrypted container was opened
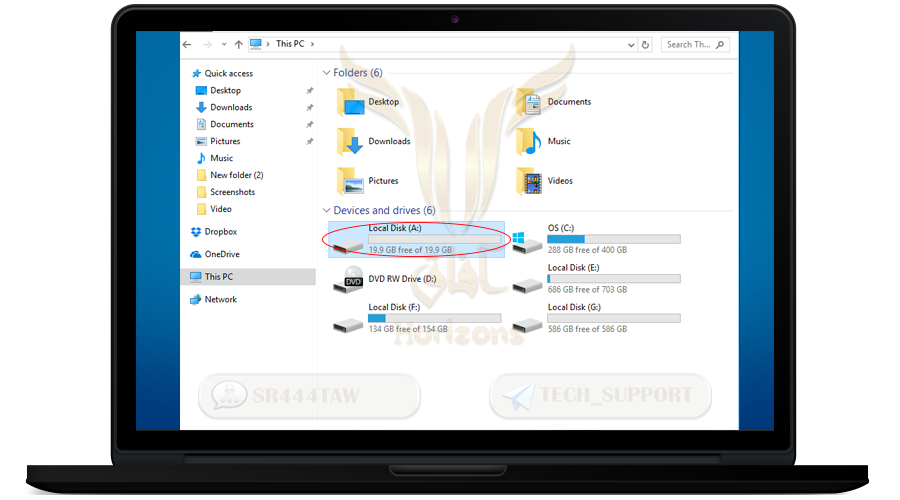
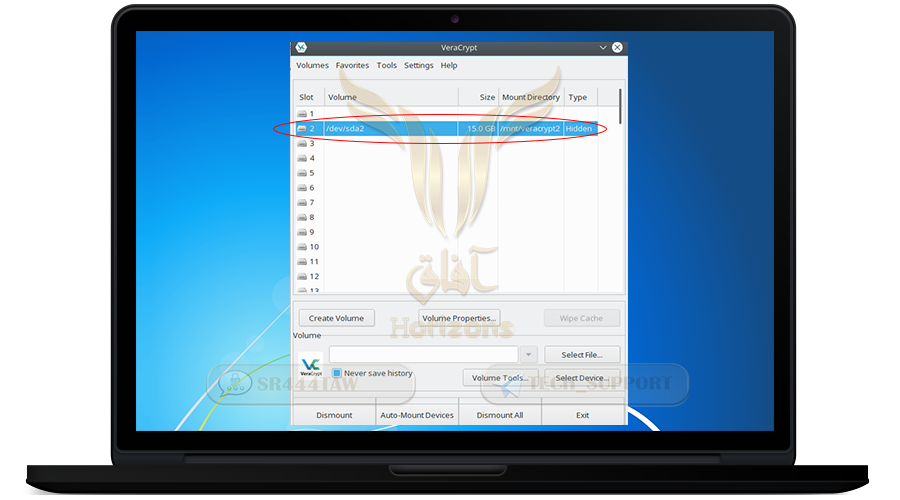
❍ Now go to my computer and you will see a new partition
❍This is how the encrypted container will look when we want to use it
❍ Now move your important files to disk A: (encrypted container)
❍ After the files moving is complete, we will close the container again so that no one can see your files if your home has been raided by enemies
(we will not open the container unless we have a job or want to use the files inside it)
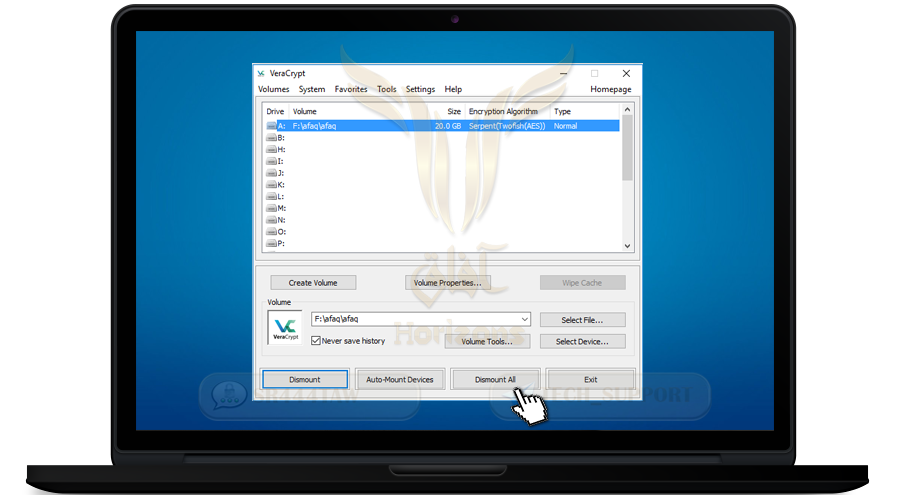
❍ Go back to the program interface and press Dismount All and the disc will disappear
❍ The container will be closed
❍ Go to the discs to make sure the container disc disappears
-------------------------------------------------------------------
Fourthly: Hide the container and program
------------------------------------------------------------------------
Step 1: Change the container icon
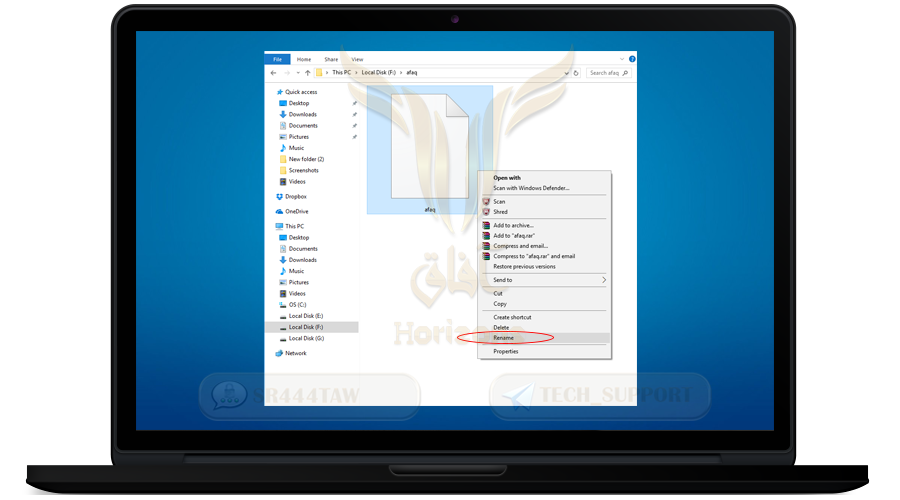
❍ Now we will fool the enemies and we change the name of the container and make its extension, for example in the format of Mp3, png or jpg
❍ Right-click and select Rename
❍ Put any name and make the file type Png as example
❍ The container folder will appear as an image icon
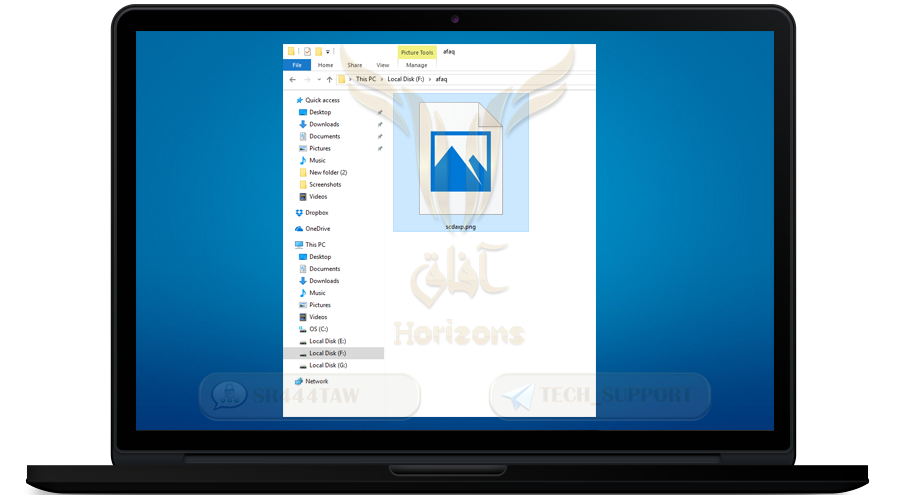
Step 2: Hide vera crypt from the control panel
❍ We will download a small program that hides the programs installed on the device from the control panel
❍ To download hideprograms click here and then continue the installation steps
❍ Click Next
❍ Click Next
❍ Click Install
❍ Then click Finish
❍ This is the program interface
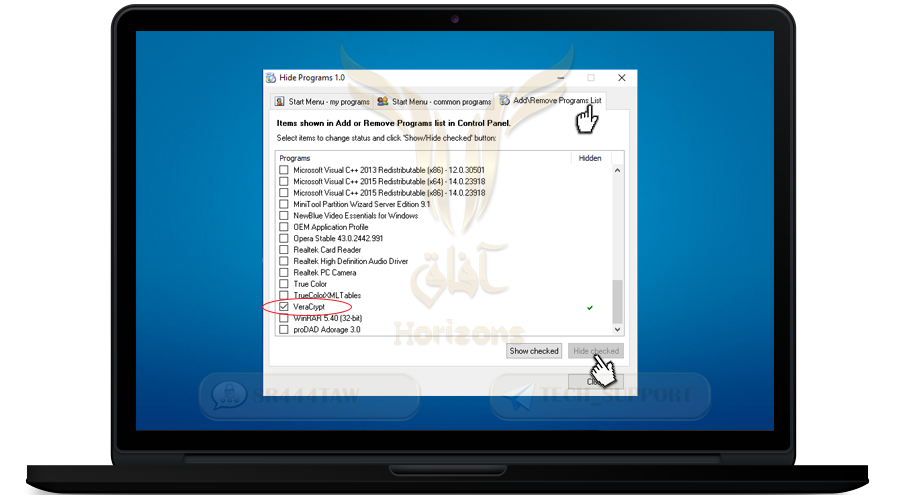
❍ Press Add / Remove Program List
❍ Then mark on VeraCrypt and click Hide checked
❍ Then go back to the control panel and make sure VeraCrypt disappears
Step 3: Hide the veracrypt.exe program that is used to open and close the container
❍ Go back to the veracrypt.exe program file in which we will open and close the container
❍ First change the folder name
❍ Then place it in the appropriate place in the computer
❍ We will change the name and icon of the program so that we deceive the enemies and prevent them from knowing the existence of the program in the computer
❍ To do this, first download Resource Hacker program from here
❍ Once the download is complete, open it and continue the steps
❍ Click Next
❍ Click install
❍ Click Finish
❍ To confirm the installation you will find the Resource Hacker program in the Start menu
💡 Important Note:
In order to change the basic icon of the YeraCrypt file, a .ico file is required
You can search for them in icon download sites such as iconarchive.com or flaticon.com
(Steps to download icon in .ico format)
❍ Go to site and click on the image to downlload
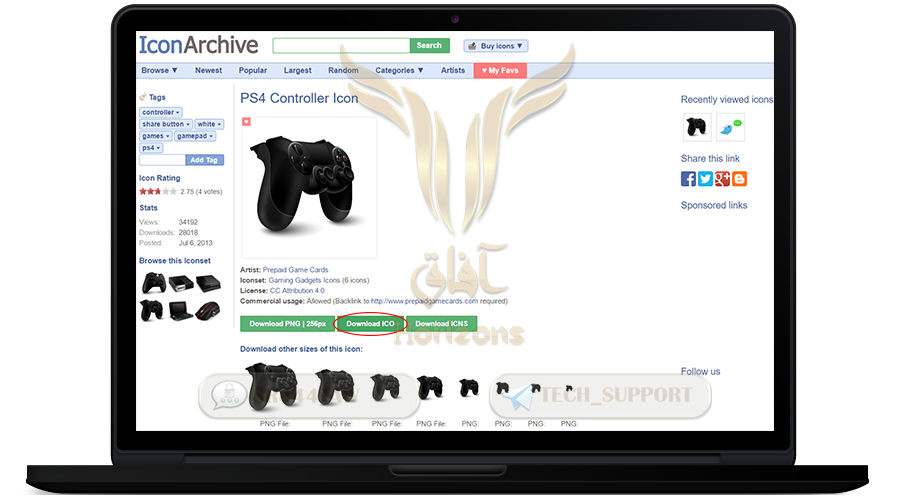
❍ Select Download ICO as specified in the image
❍ Right-click on VeraCrypt to change the icon
❍ Choose Open using Resource Hacker
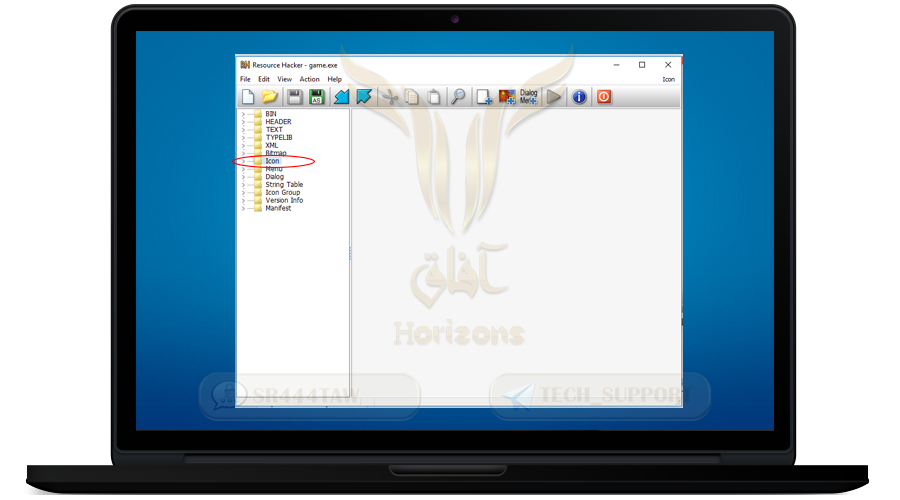
❍ This is the interface of the Resource Hacker program
❍ Select the Icon folder
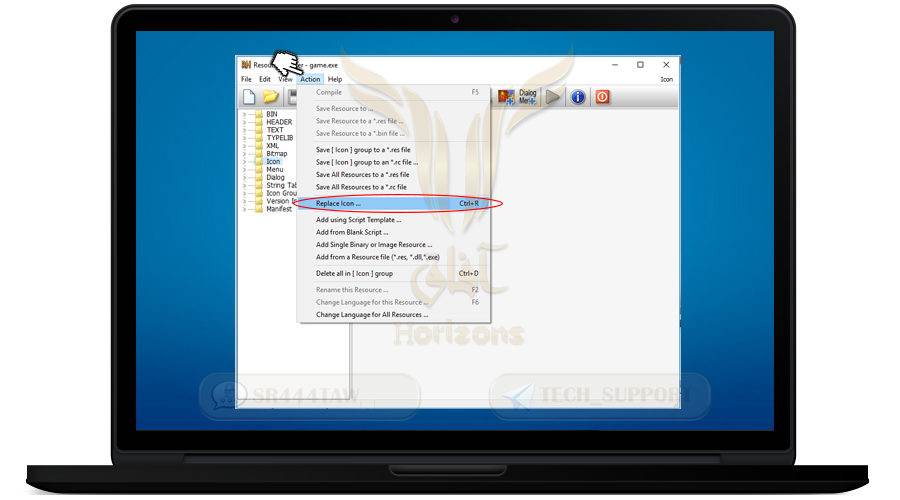
❍ Then in the menu click on the Action option and choose Replace Icon
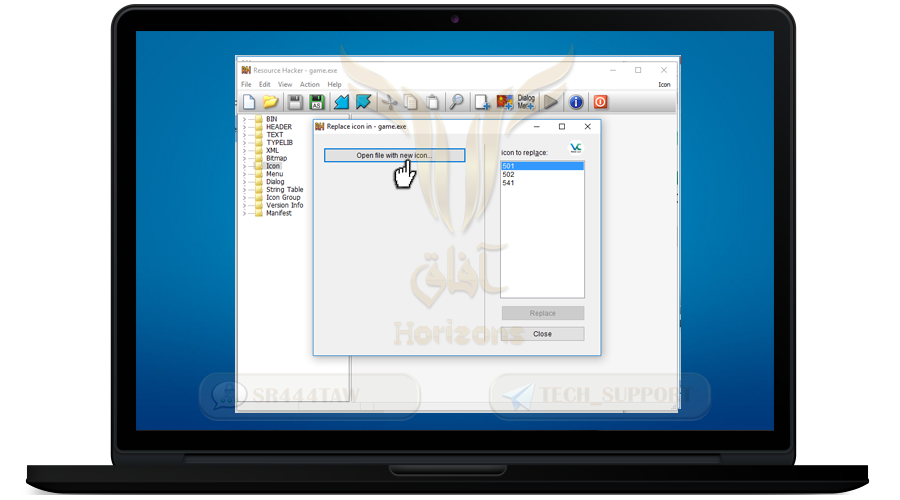
❍ Click Open file with new icon
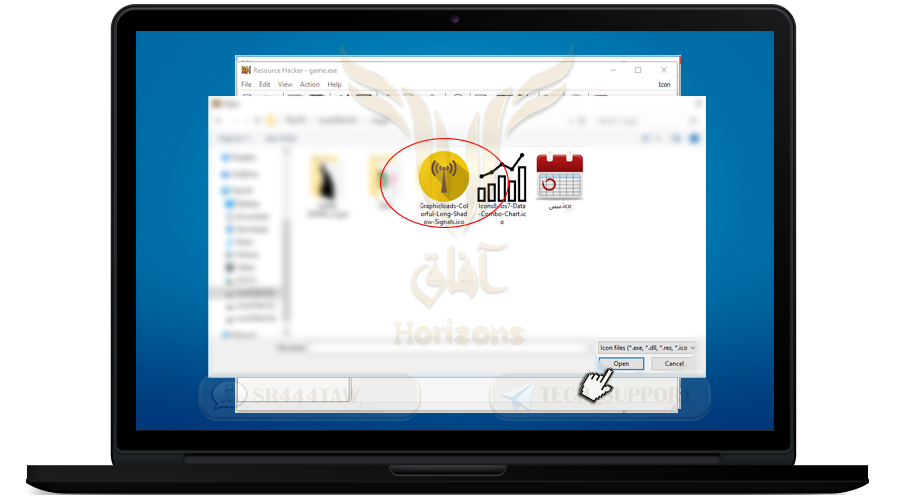
❍ Select the image icon you want to place instead of the basic icon
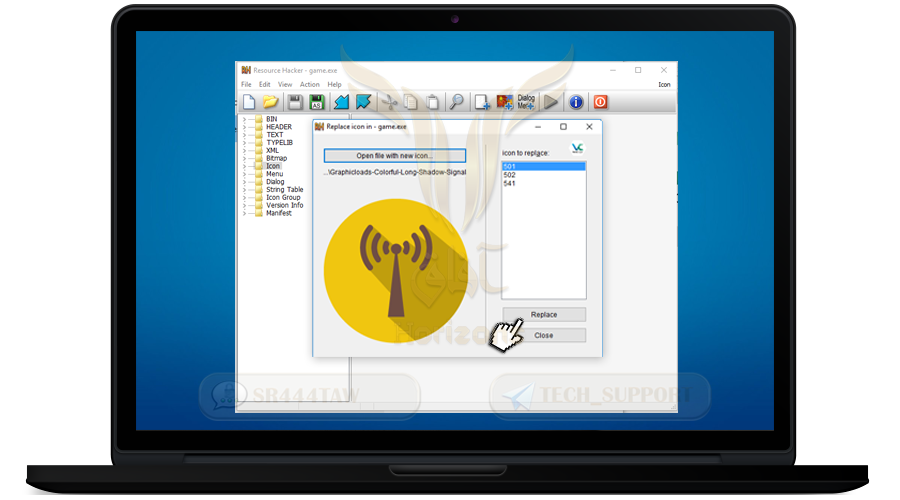
❍ then press OPEN
❍ Press Replace
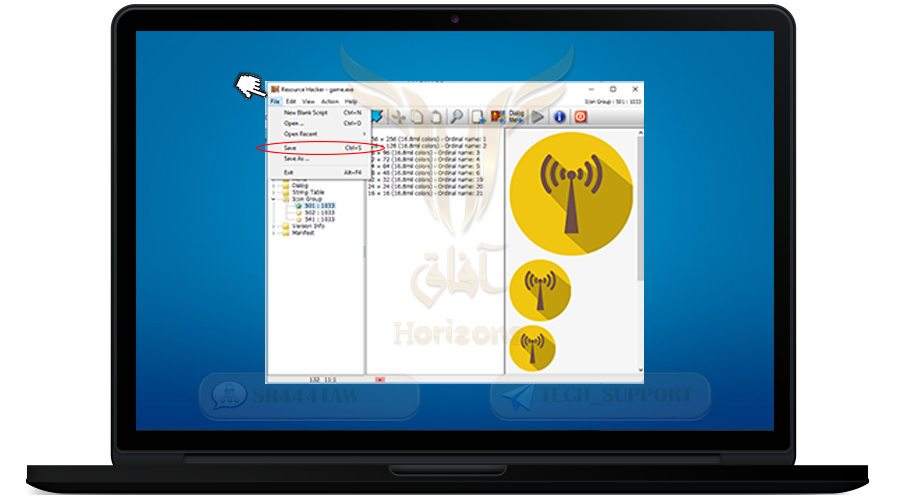
❍ Then select File option from the menu
❍ Press Save to save your changes
❍ Then restart the computer and you will find the icon has changed
❍ We then change the VeraCrypt name to any appropriate name with the icon you set
💡 Note:
Resource Hacker will make a copy of the program, delete it and leave only the version you have changed its icon
----------------------------------------------------------------------------------------------
Fifthly: Set up a hidden container (extra) inside the main container
------------------------------------------------------------------------------------------------------
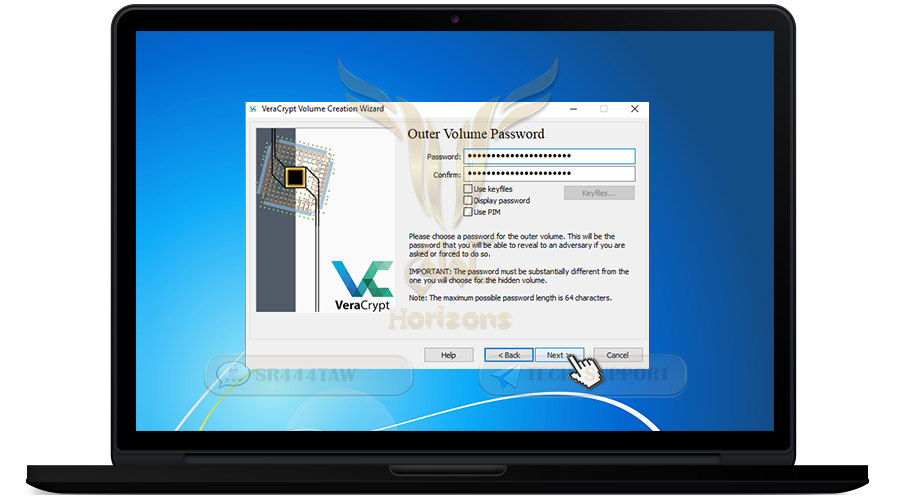
Veracrypt allows you to hide the folder of the container by setting a different password with the main container folder. Even if you are arrested and forced to give the password, you have the option to display the general password for the main container folder, not the extra container or hidden folder
The difference between the main container folder and the hidden container folder is the password difference. Each folder has its own password
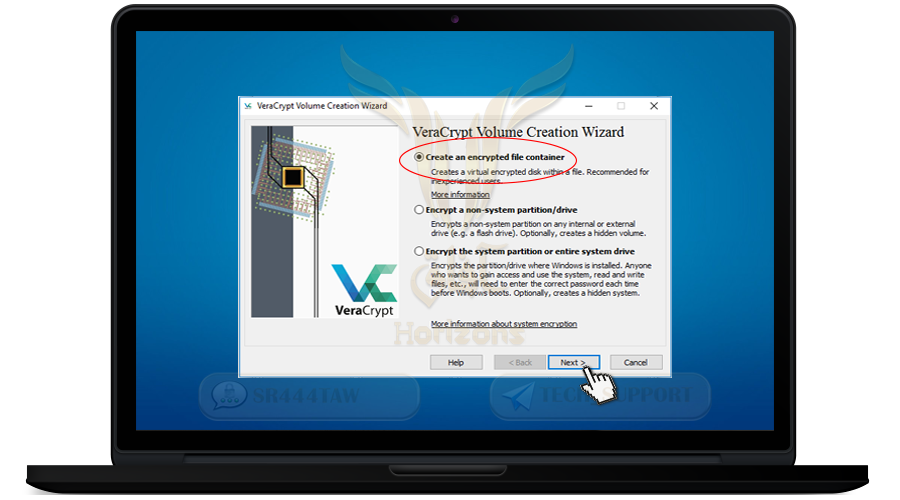
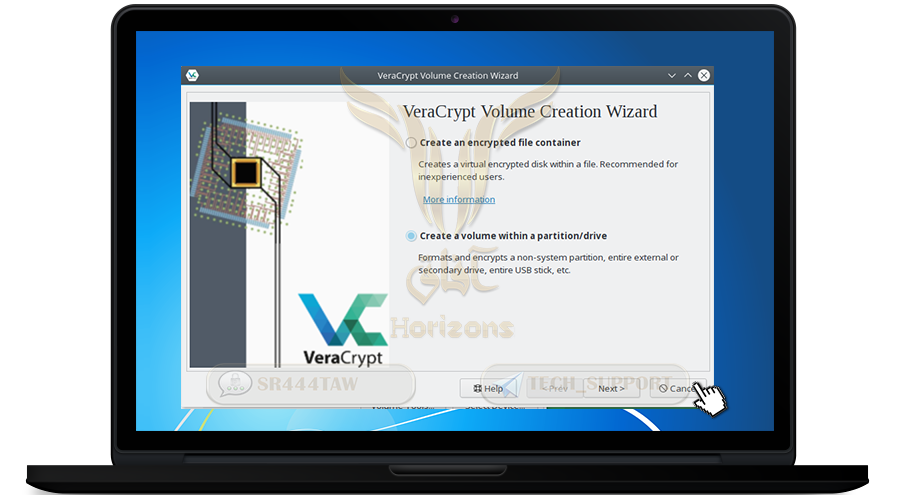
❍ Select Create Volume
❍ Select Create an encrypted file container and then click Next
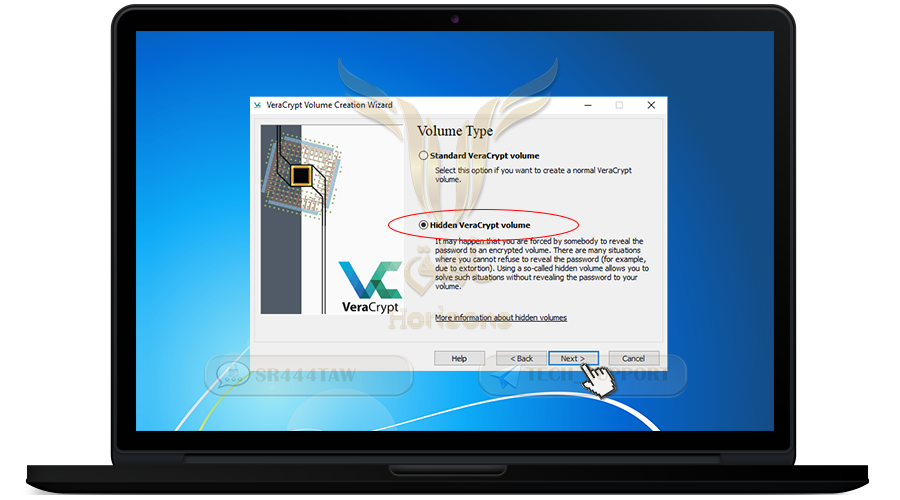
❍ Select Hidden VeraCrypt volume to create an additional hidden container within the main container folder
❍ Then click Next
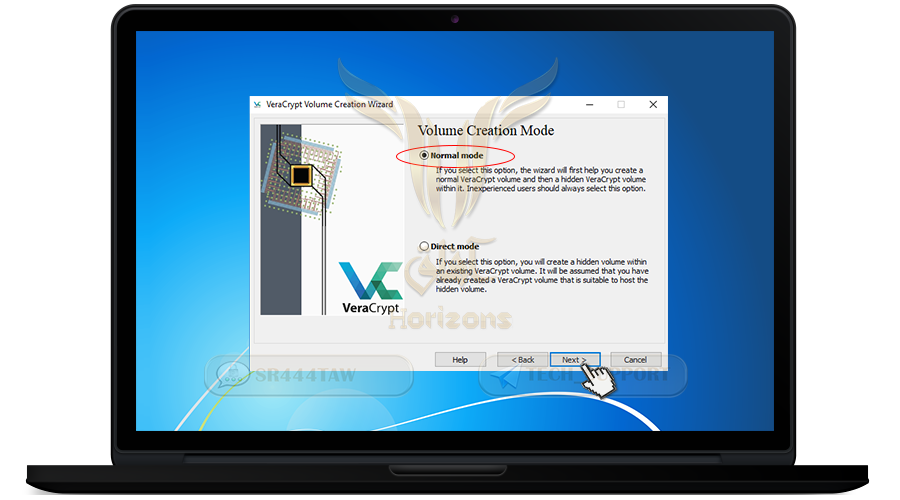
❍ Select Normal mode
❍ Then press Next
❍ Press Select File and choose the location and name of the main container in which we will put the extra container to save files
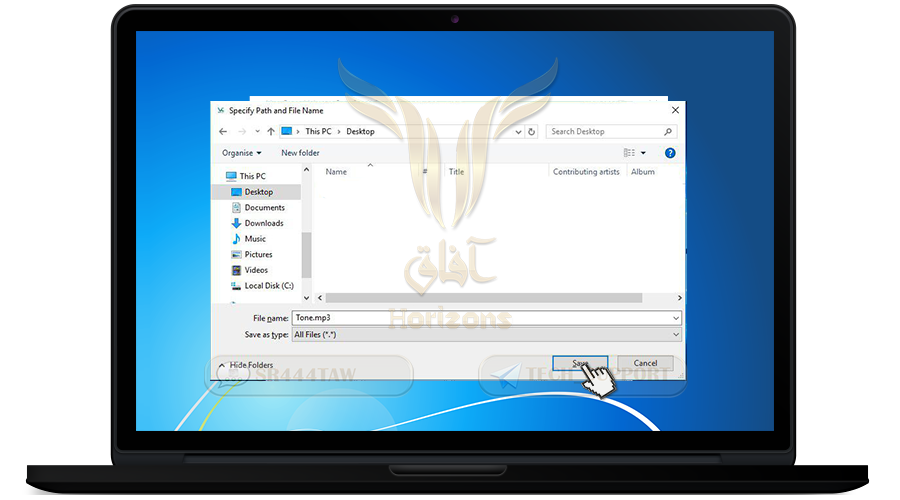
❍ We will choose the container format of Mp3 or PNG for camouflage as in the picture
❍ Press Save
❍ After selecting the name and location of the container, click Next
❍ Click Next
❍ Select the size of the main container
❍ Then click Next
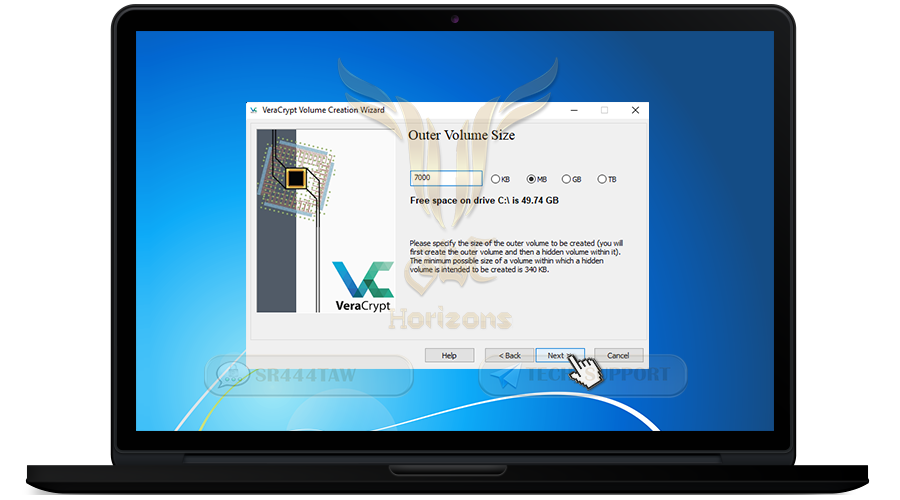
❍ Now we will choose encryption algorithm
❍ Select AES-Twofish-Serpent, this option to encrypt files with 3 algorithms, if the attacker can decrypt one algorithm will not be able to decrypt the other algorithms
❍ Then click Next
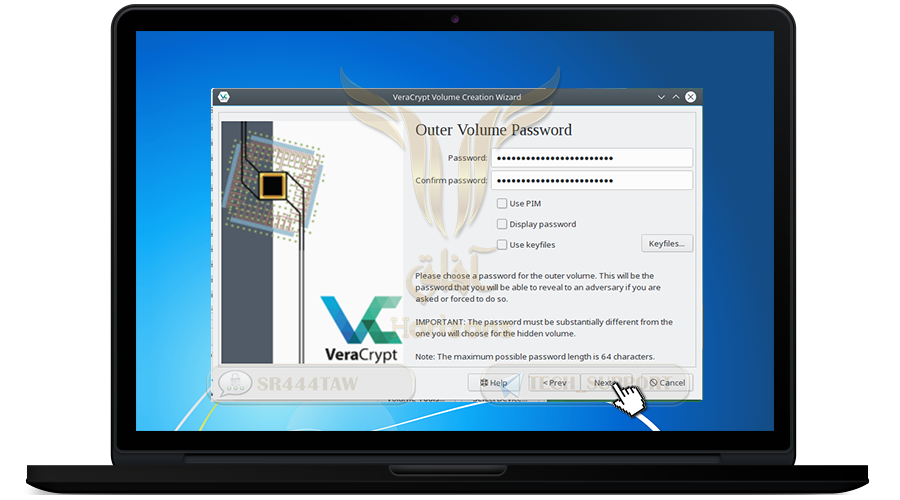
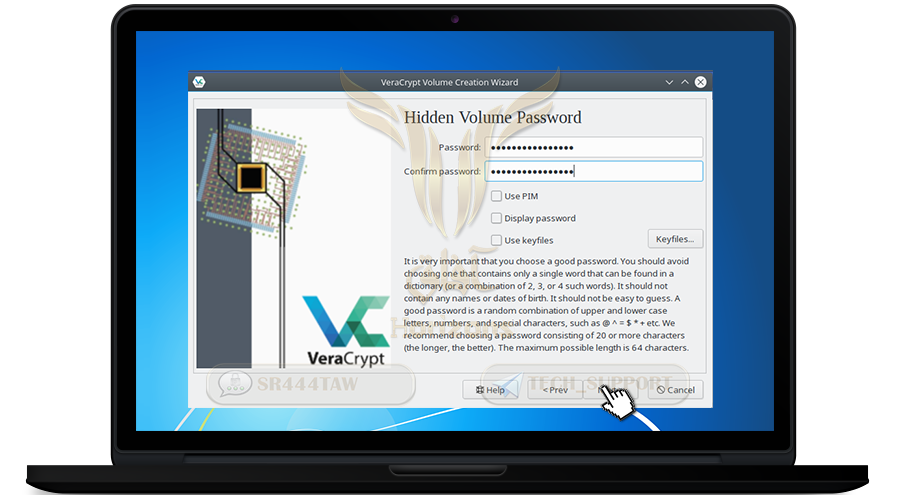
❍ Enter a strong password and confirm it in the second box and press Next
💡 Note:
You can also add a file or image or code if you have lost the container password (optional) where the file serves as a key to open the folder of the hidden container
❍ To add a file or image mark Use key files option and press Key file
❍ Select the file or image or PGP key and press OK
❍ Click Next
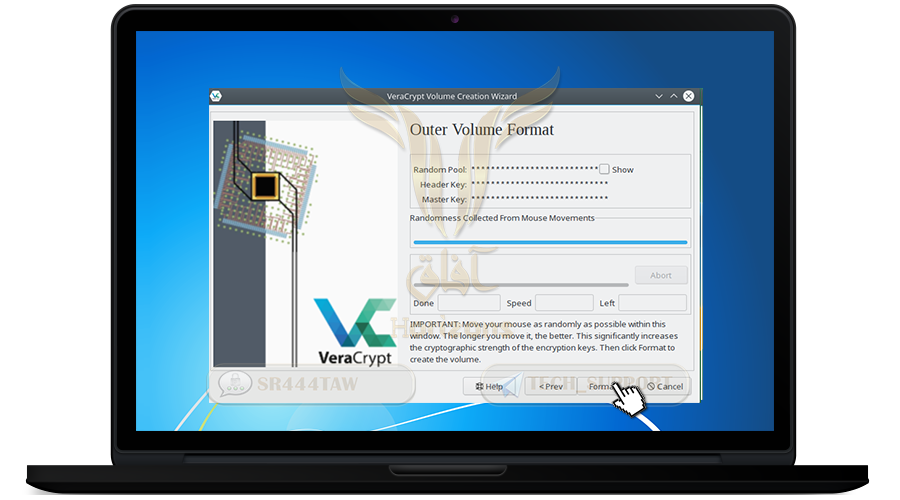
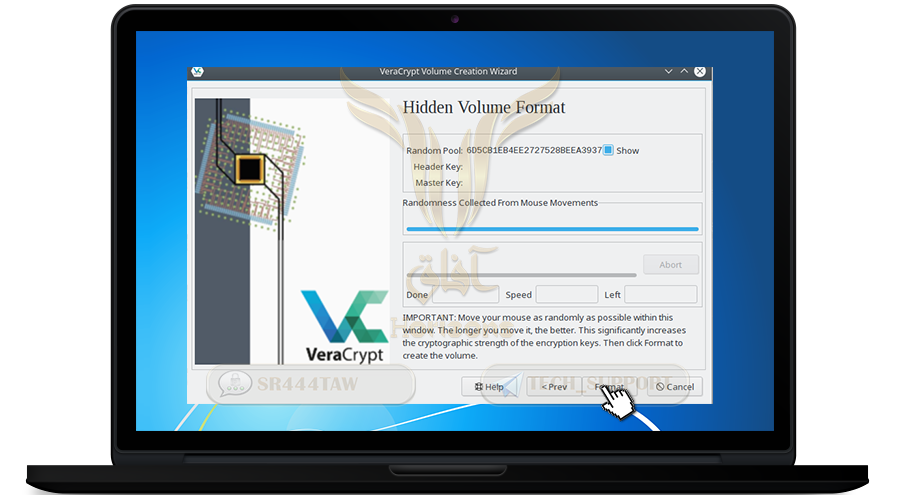
❍ Now the program will encrypt the container file. move the mouse randomly

❍ Then press Format and wait until you finish creating the main container
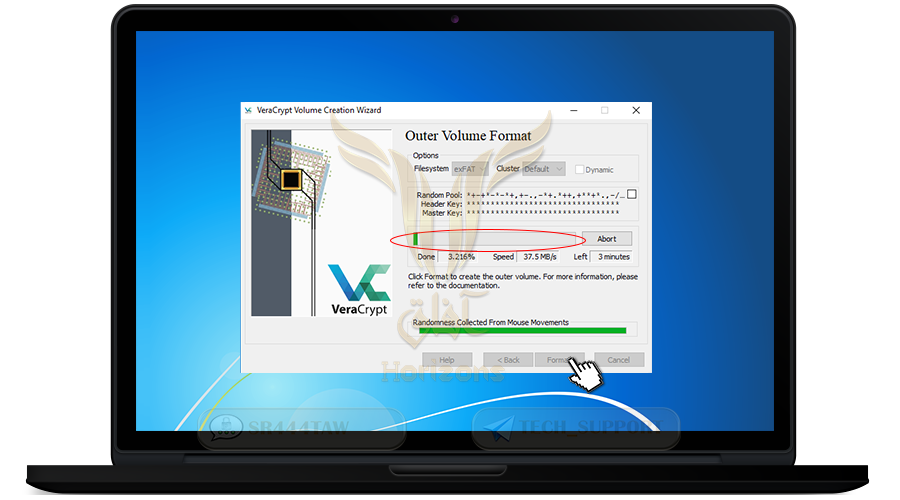
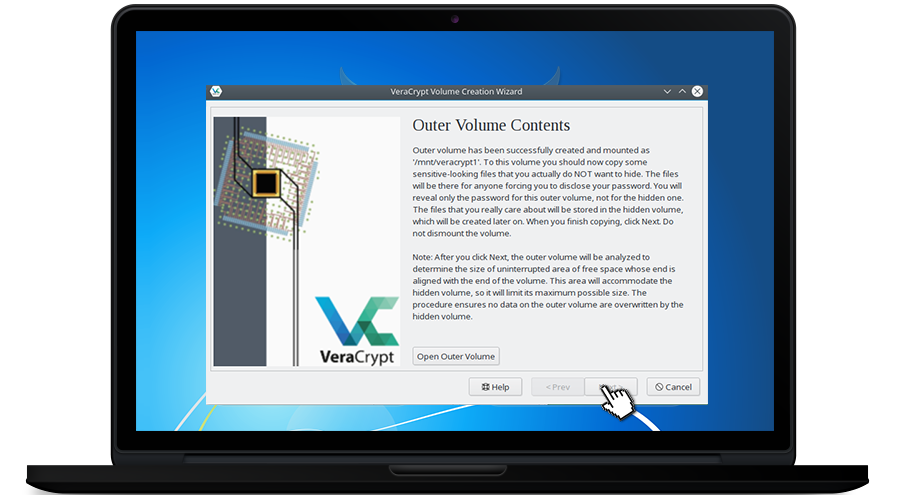
❍ Thus the main container was created which is (Z)
❍ Click on Open Outer Volume and add files to it
💡 Note
You must add as many files as possible in the main container folder before creating the hidden container folder, because adding files to the public container folder after creating the hidden container folder may cause the hidden container folder to be corrupted.
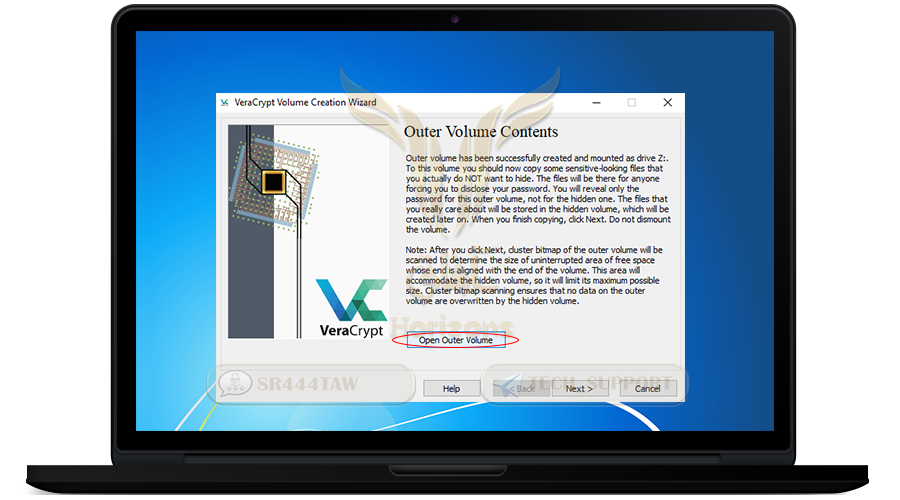
❍ We will place these two files inside
❍ Then close the window
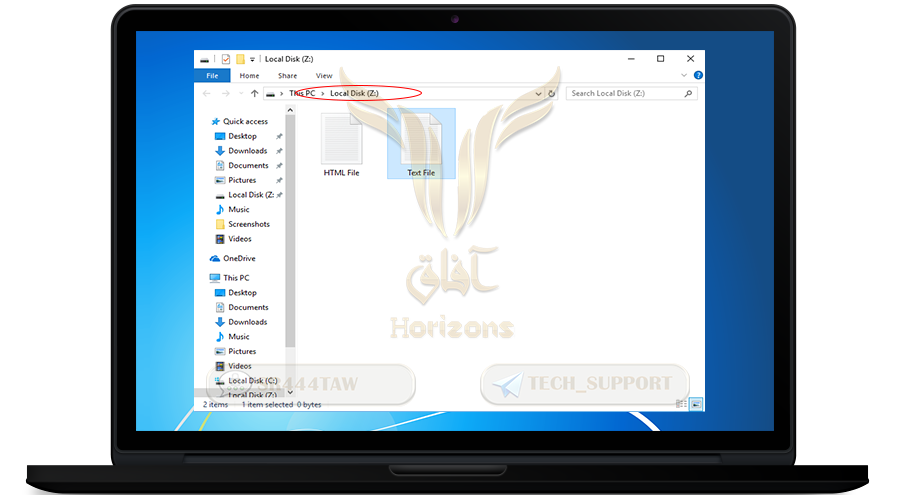
❍ Now the hidden container will be created (extra)
❍ Click Next
❍ Press Yes

❍ Select Yes then press Next
❍ Select AES-Twofish-Serpent again
❍ Then click Next
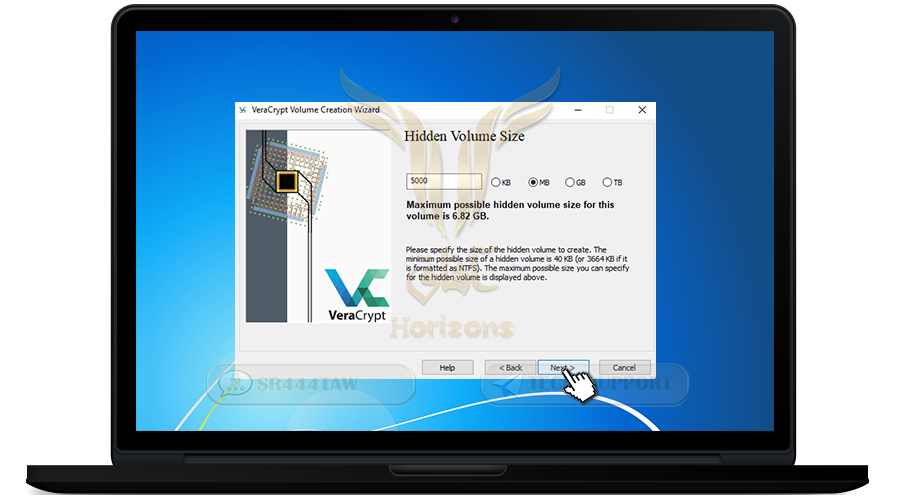
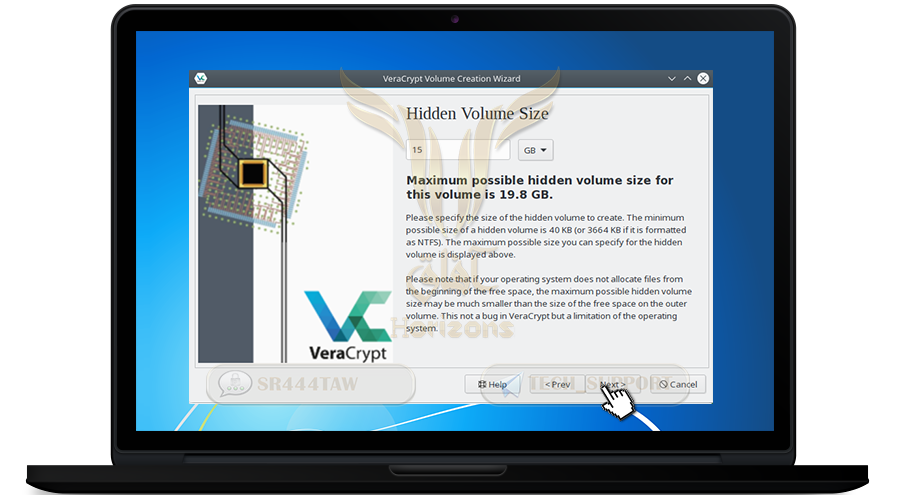
❍ Determine the size of the hidden container (less than the size of the main container)
❍ Click Next
❍ Move the mouse as in the previous steps
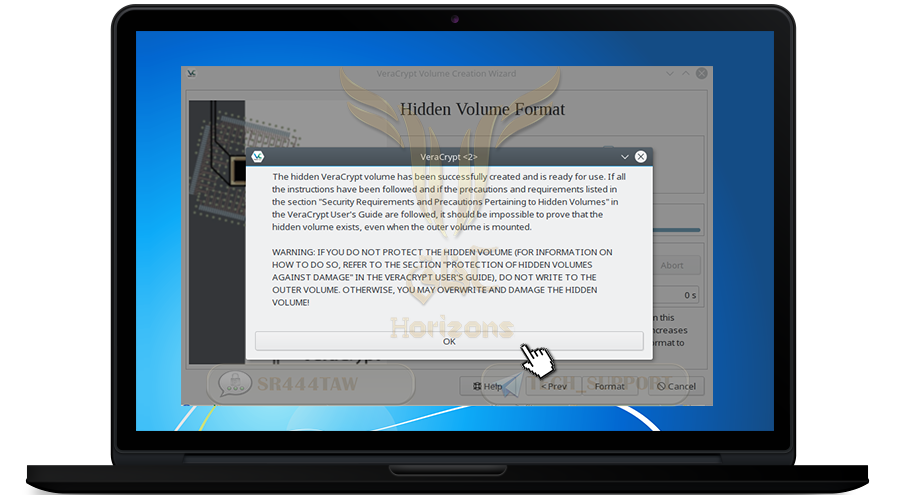
❍ Then press Format and wait until you finish creating the hidden container
❍ Press OK
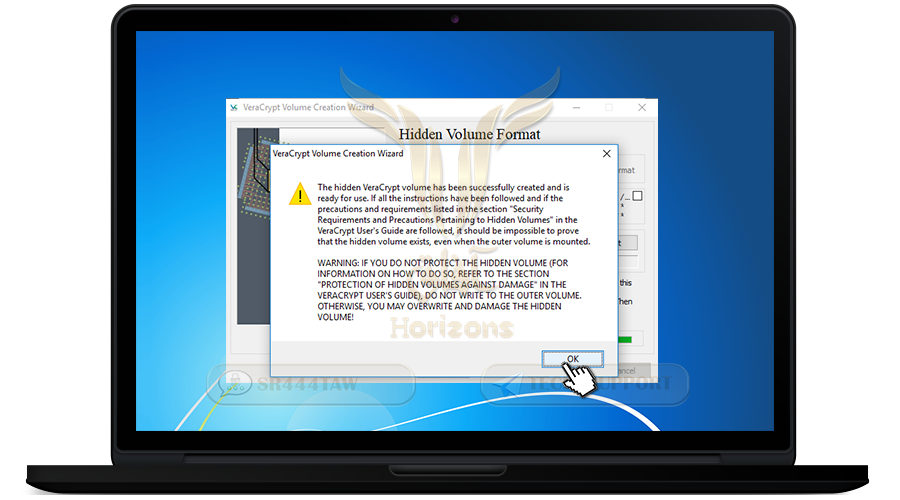
❍ The creation of hidden container (extra) is completed

❍ Close the window
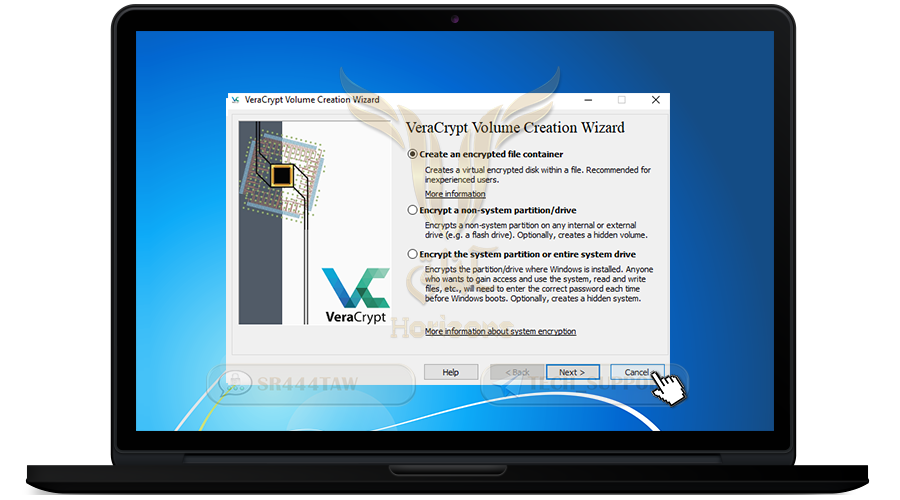
❍ Open VeraCrypt
❍ choose Select File
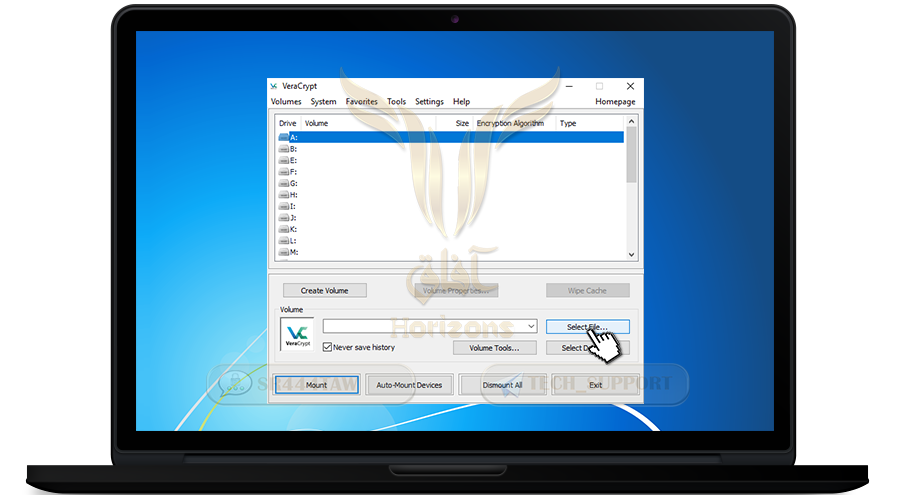
❍ Select the container you have created
❍ Now you have two containers, a main container and an additional hidden container, you can open either of the two containers by entering their password
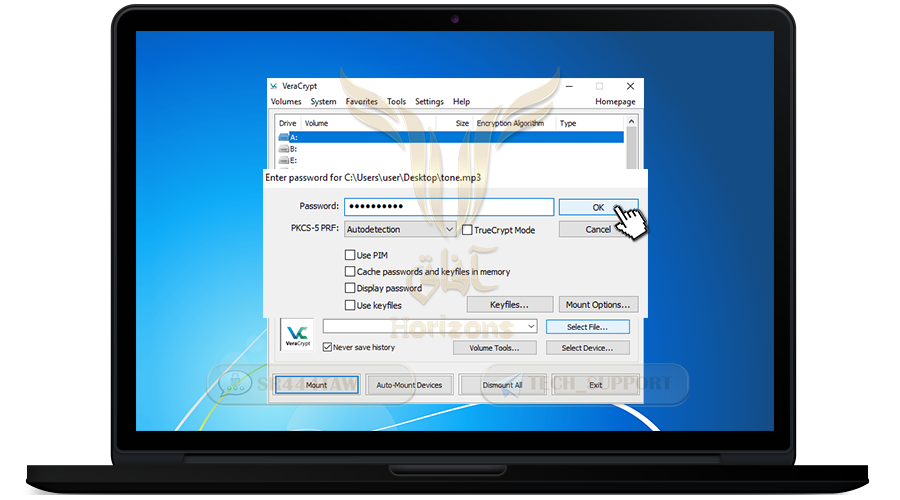
💡 Note
The utility of the additional container is that if you are forced to give the password to the main container during interrogation, they will not be able to tell that there is another hidden container
❍ We will open the main container after entering its password and press Ok
❍ This will open the main container (Z) in which we placed the files when they were created
❍ But If we enter the hidden container password, it will appear blank because we have not added the files yet
❍ After the files moving is complete, we will close the container again so that no one can see your files if your home has been raided by enemies
💡 Note
we will not open the container unless we have a job or want to use the files inside it
❍ Go back to the program interface and press Dismount All and the disc will disappear
----------------------------------------------------------------------------------------
sixthly: How to encrypt System disks and External Memory
-----------------------------------------------------------------------------------------------
The utility of encrypting external USB memory and system disks is not only hidden, but encrypted so that you can use the same steps to encrypt your disks when choosing Standrad VeraCrypt volume and not hidden VeraCrypt volume and will not be able to retrieve any of the software .. You can also split the external memory and make it two disks, Hidden and disc visible as in the following steps
❍ Select Create Volume
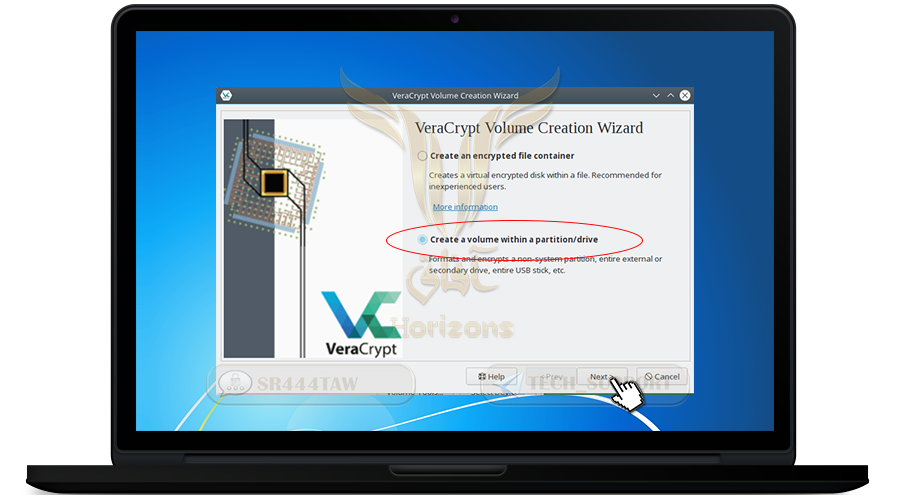
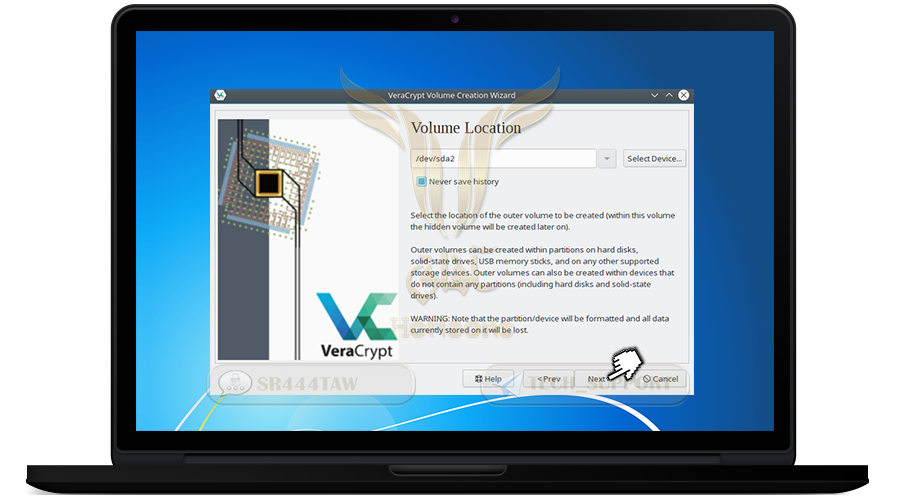
❍ Select Encrypt a non-system partition / drive and click Next
❍ Select Hidden VeraCrypt volume to create an additional hidden disk inside the primary disk or memory
❍ Then click Next
❍ Select the disc you want to encrypt and hide and press OK
❍ Click Next
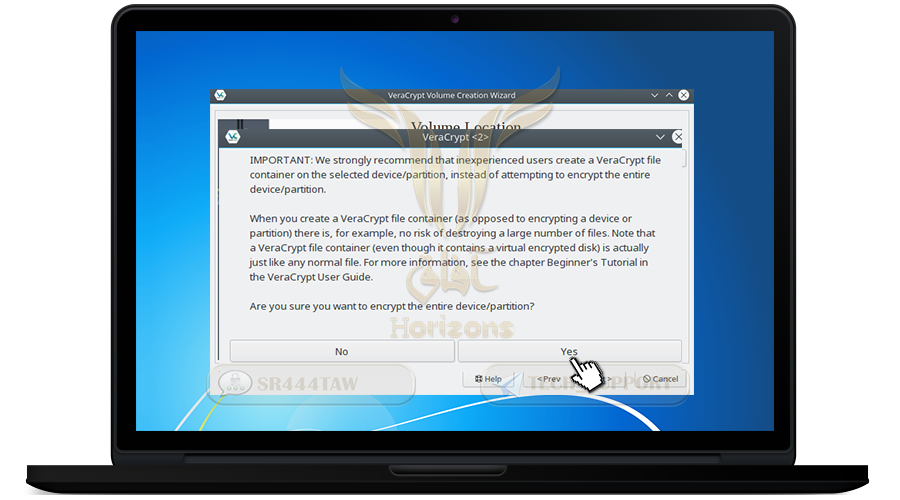
❍ Press Yes
❍ Press the indicated position to select the encryption algorithm
❍ Select AES-Twofish-Serpent, this option to encrypt files with 3 algorithms, if the attacker can decrypt one algorithm will not be able to decrypt the other algorithms
❍ Then click Next
❍ Enter a strong password and confirm it in the second box and press Next
💡 Note:
You can also add a file or image or code if you have lost the container password (optional) where the file serves as a key to open the folder of the hidden container
❍ To add a file or image mark Use key files option and press Key file
❍ Select the file or image or PGP key and press OK
❍ Now the program will encrypt the disc or memory. Move the mouse randomly until the line is completed
❍ Then press Format
❍ Press Yes
❍ Thus the disk or memory has been encrypted
❍ Click on Open Outer Volume and add files to it
💡 Note
You must add as many files as possible in the main container folder before creating the hidden container folder, because adding files to the public container folder after creating the hidden container folder may cause the hidden container folder to be corrupted.
❍ Then click Next
❍ Now the disc will be created (extra & hidden) inside the main disk
❍ Click Next
❍ Select AES-Twofish-Serpent again
❍ Then click Next
❍ Specify the size of the additional disc hidden (size less than the disc)
❍ Click Next
❍ determine the size of the additional disc hidden (less than the main disc size)
❍ Click Next
❍ Enter a strong password and confirm it in the second box and press Next
❍ Now the program will encrypt the hidden disk (extra) inside the primary disk. Move the mouse randomly until the tape is completed
❍ The program will encrypt the hidden disk (extra) inside the primary disk. Move the mouse randomly until the tape is completed
💡 Note:
move all your files from disk or USB stick before Encryption because encryption will delete all disc content
❍ Then press Format and wait until you have finished creating the extra disk
❍ Press OK
❍ Close the window
❍ Open VeraCrypt
❍ Select auto-mount devices
❍ Now if you want to open the main disk or memory enter the password you entered when encrypting the disk
❍ If you want to open the additional hidden disk, enter the container password
❍ Thus the disk was opened
❍ To close the disc Press on "dismount all"
💡Explain:
* To restore the disks to the first mode without encryption, you must format them using Mini Tool Partition wizard program
* If you want to use the encrypted USB on another computer, you must install Veracrypt in that computer because you can not run the encrypted USB on any other computer except Veracrypt on the computer
❊❊❊❊❊❊